In this article
- How Did Phishing Start?
- What Is Phishing?
- 5 Categories of Phishing
- Types of Phishing Attacks
Blog Articles
Article at a glance
The article explores the evolution of phishing, starting with early techniques like algorithm-based phishing and progressing to modern, more sophisticated forms. These attacks have become increasingly targeted and varied, including methods like voice and SMS phishing, as well as exploiting search engines and websites. The goal of these attacks is often to steal sensitive information such as login credentials, financial data, or personal details, and they can have devastating consequences for both individuals and organizations.
IT administrators are encouraged to implement multiple layers of defense, educate users, and utilize security tools to prevent these attacks. Understanding the different tactics used by phishers and staying updated on emerging threats are crucial steps in protecting organizational data and maintaining cybersecurity.
How Did Phishing Start?
1990: Algorithm-Based Phishing
2000: Email Phishing
2003: Domain Spoofing
2018: Phishing via HTTPS
What Is Phishing?
5 Categories of Phishing
1. Vishing
2. Smishing
3. Search Engine Phishing
4. Spear Phishing
5. Whaling
Types of Phishing Attacks
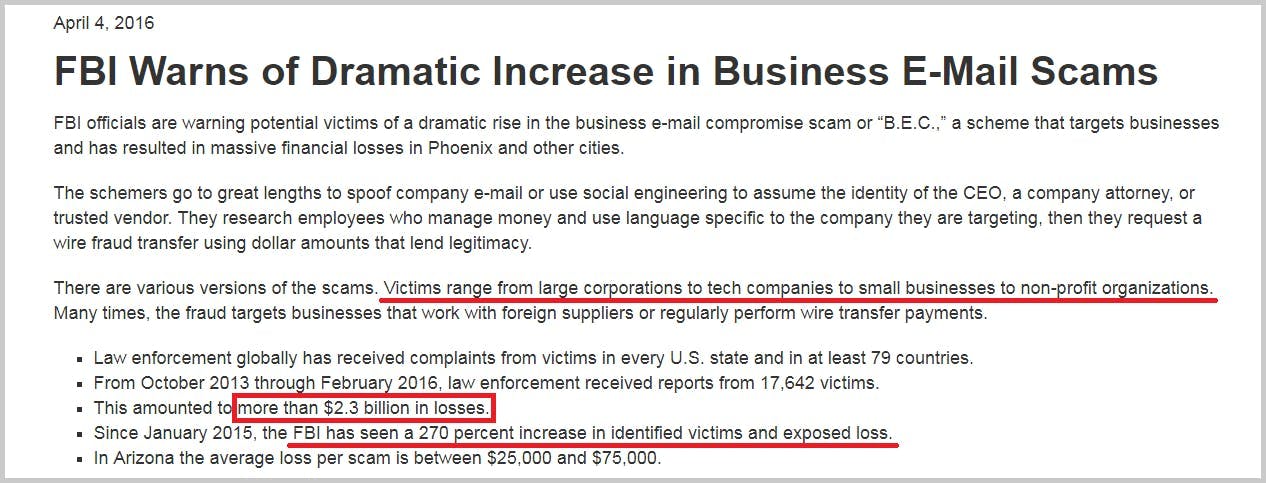
1. Email Spoofing – Name Impersonation
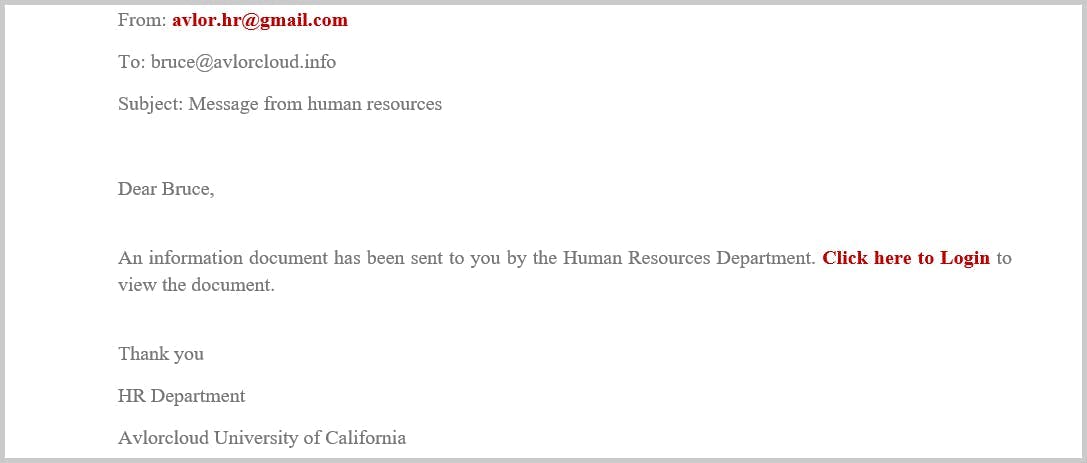
2. Mass Target – Brand Impersonation
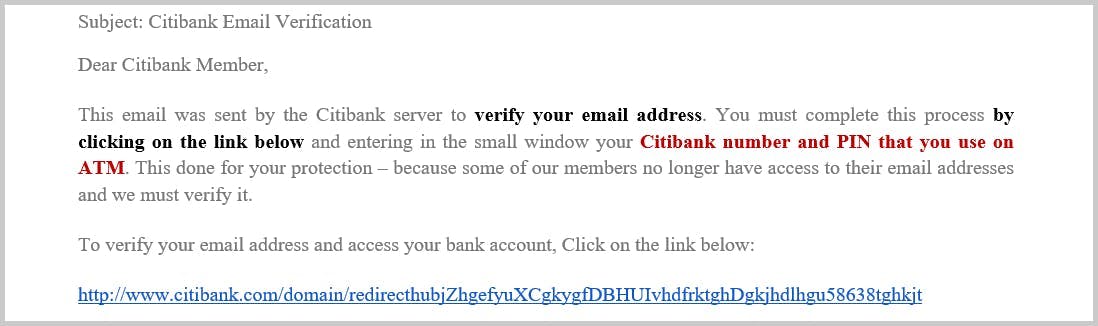
3. URL Phishing
Hidden link
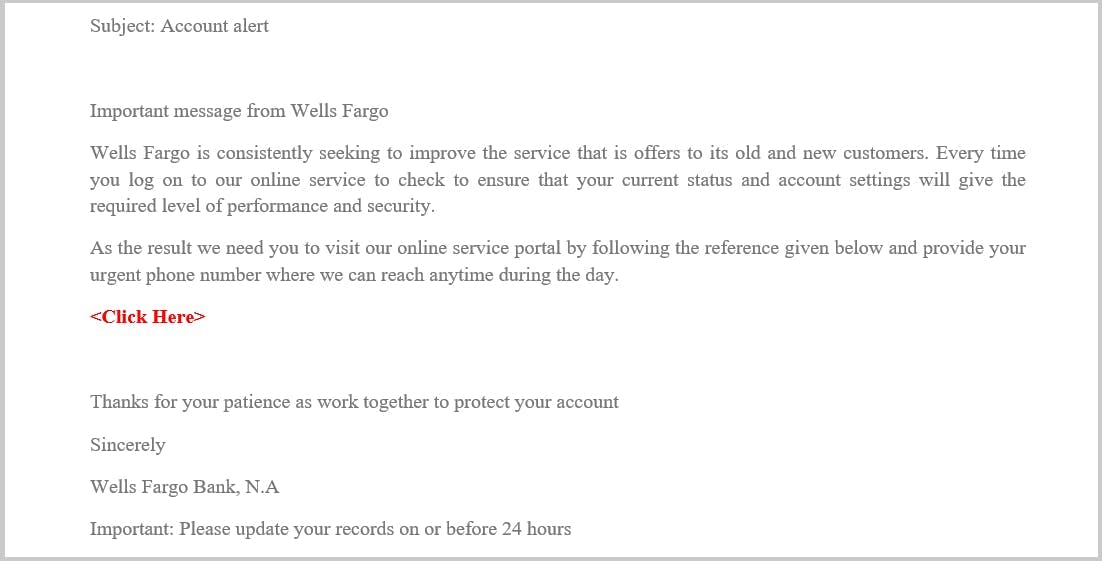
Tiny URL
Misspelled URL
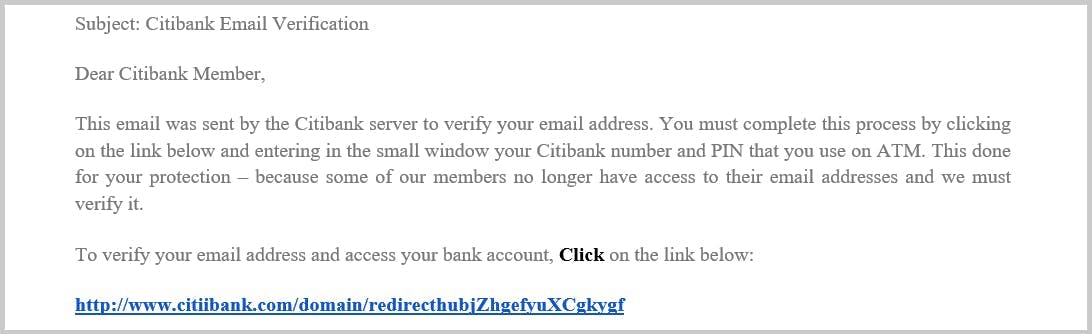
Homograph attack
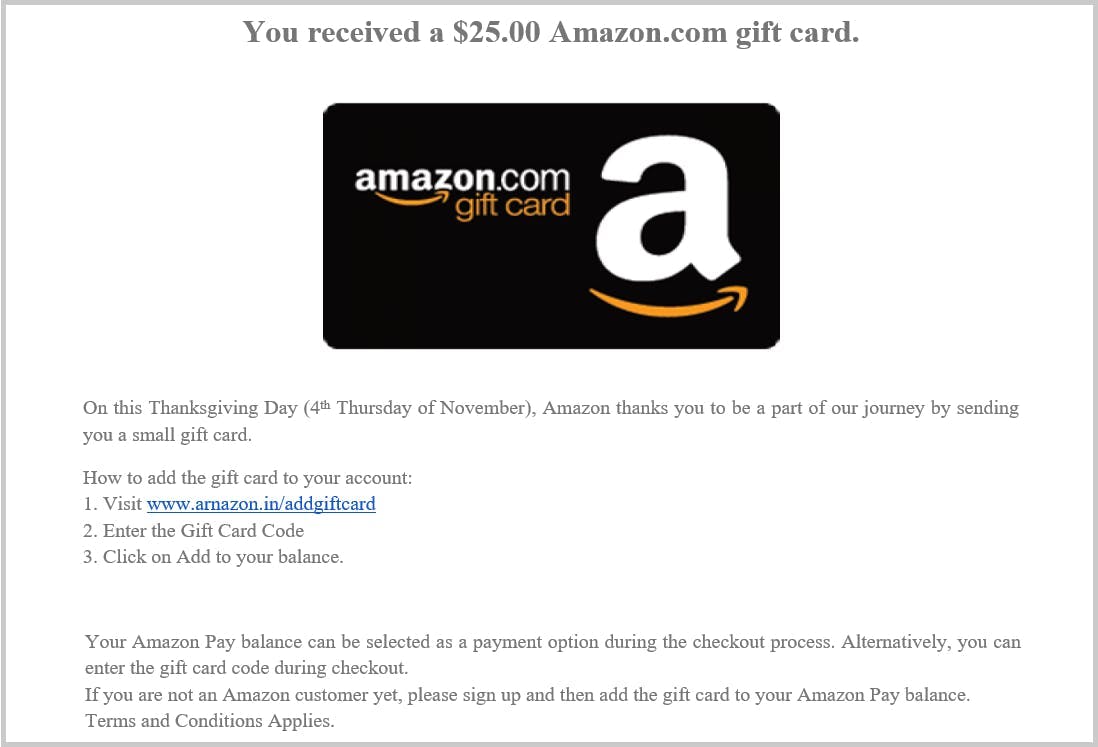
4. Subdomain Attack
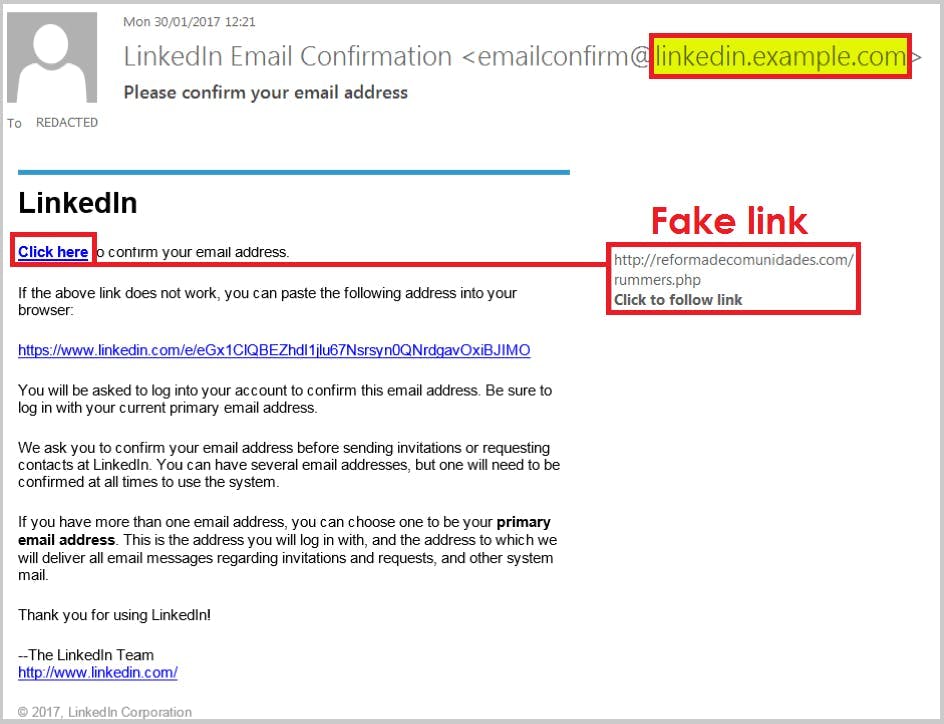
5. Pop-Up Messages: In-Session Phishing
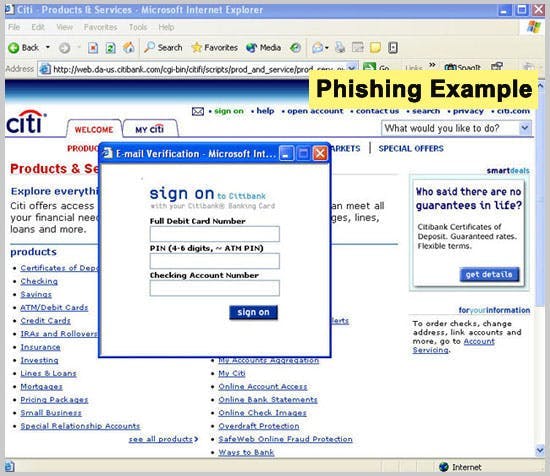
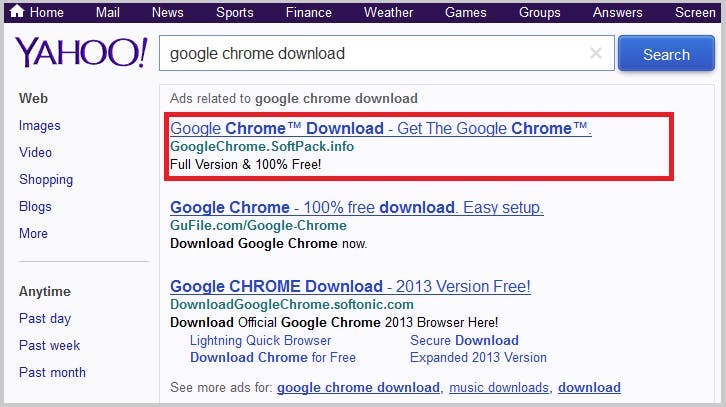
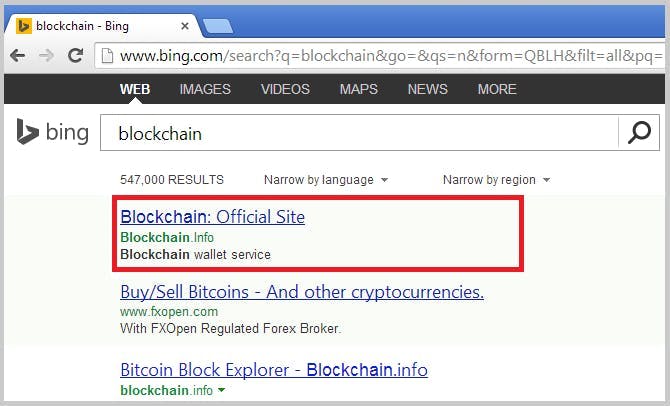
6. Search Engine Attack
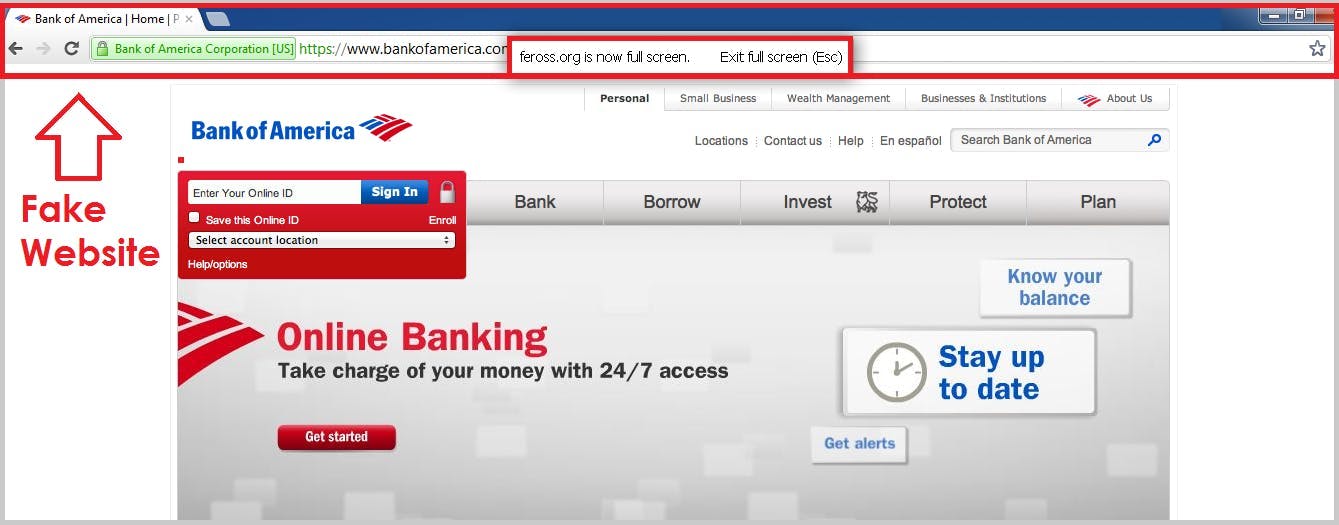
7. Website Spoofing
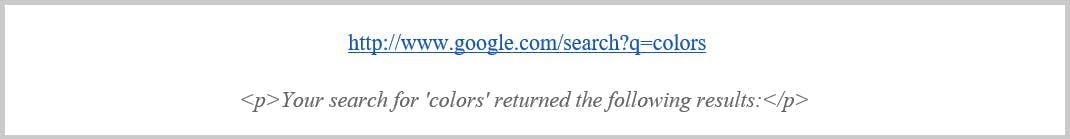
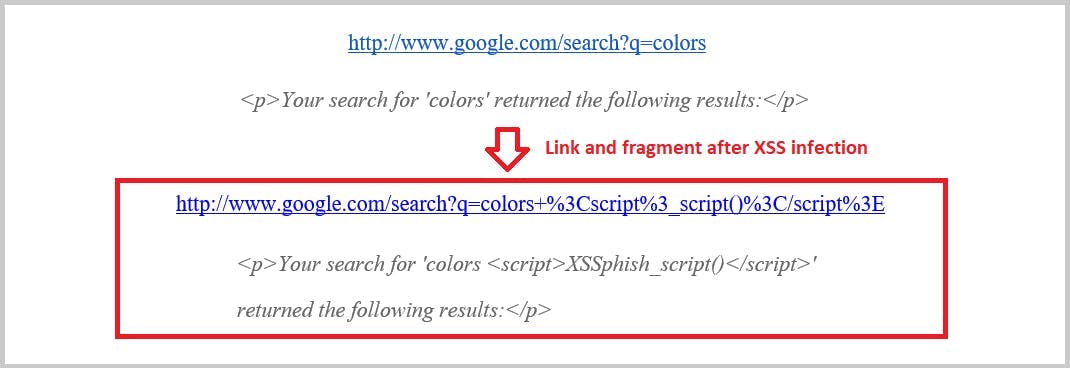
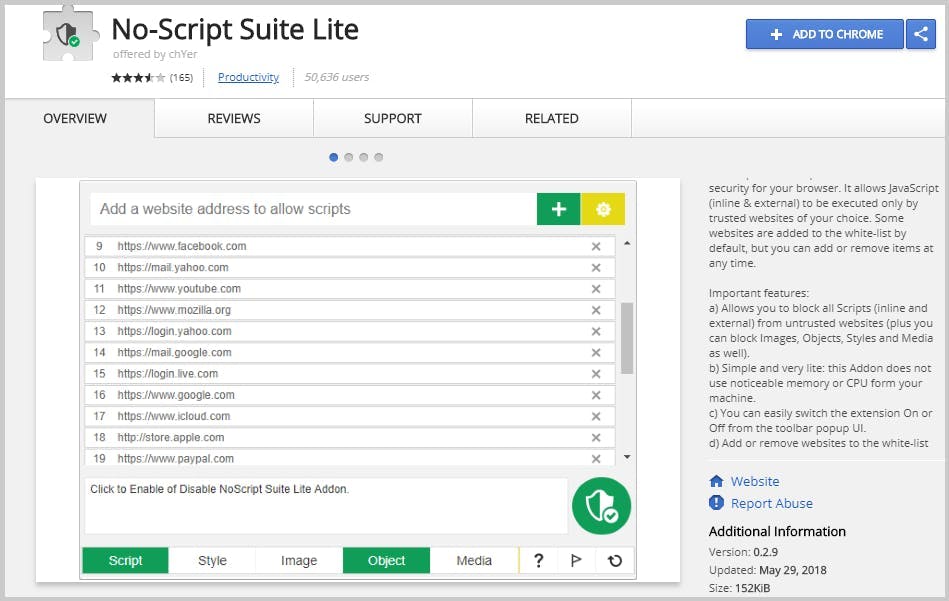
8. Scripting
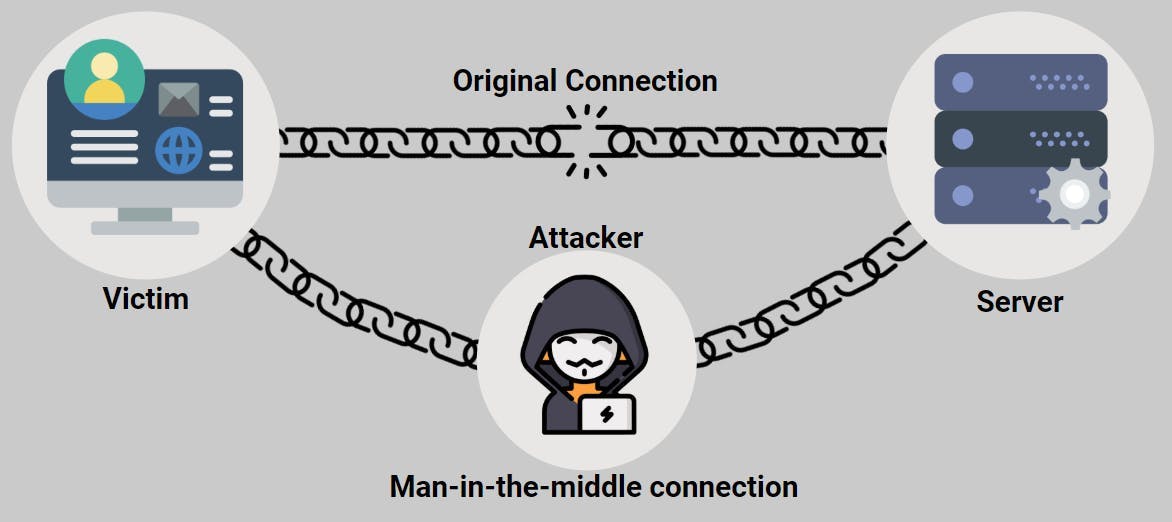
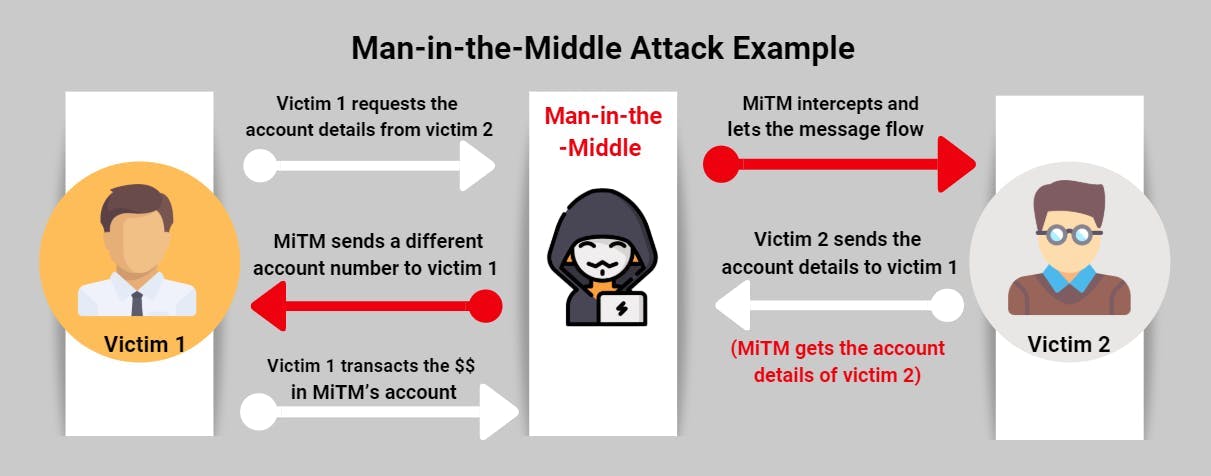
9. Man-in-the-Middle Attack
10. Clone Phishing
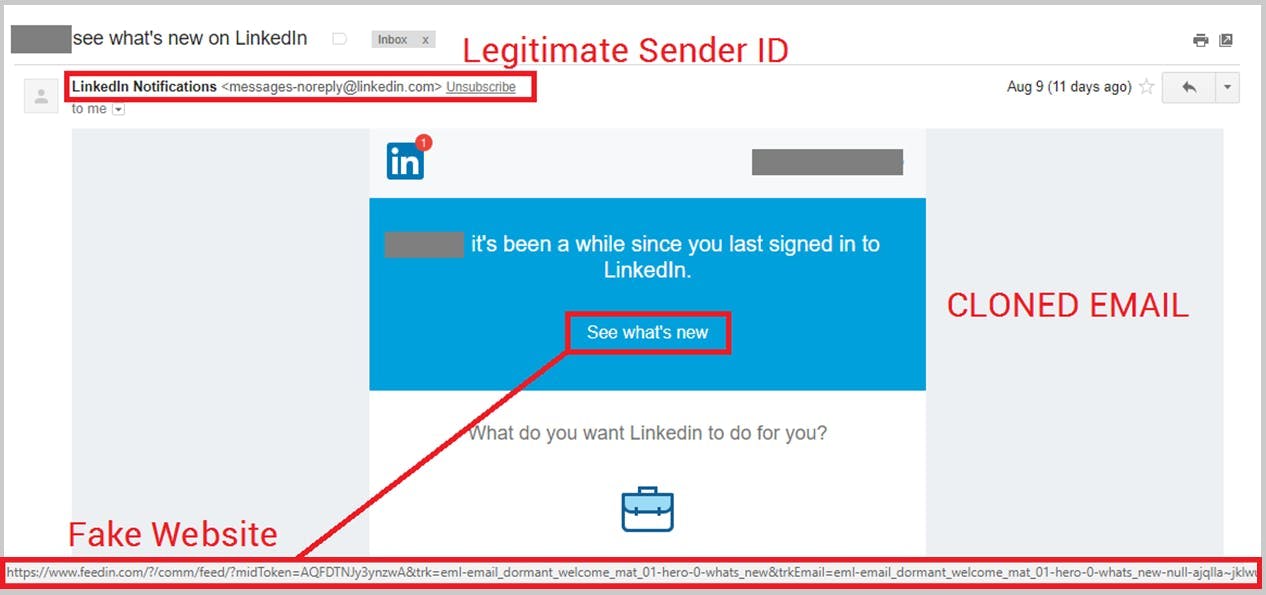
11. Image Phishing
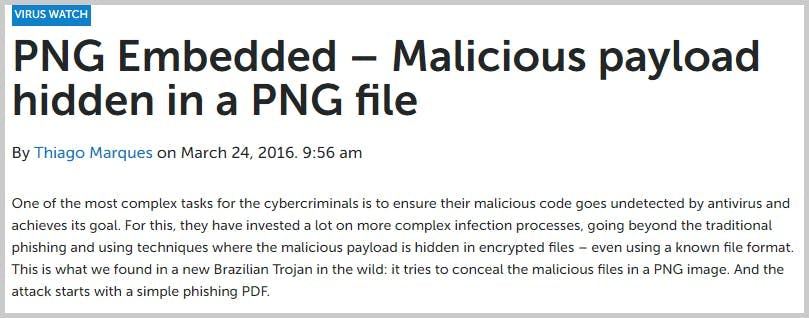
12. Voice Phishing Attack
13. CEO Fraud