In this article
- Organizational structure overview
- Building the organizational structure
- Organizational units and permissions
- Organizational units vs. access groups
- Admin role for an OU
- Data retention management
- Best practices
- FAQs
Blog Articles
Article at a glance
Google organizational units (OUs) in Google Workspace enable tailored management of user settings, access, and data retention:
- OUs allow for customized access to apps, services, and device management based on specific roles and departments.
- Data retention policies can be applied at the OU level using Google Vault, ensuring compliance and security.
- Access groups offer flexibility in managing service access without altering the OU structure.
What is the solution?
Leverage OUs for efficient management and use SysCloud for automated backups, ensuring comprehensive data protection and easy recovery.
1. An introduction to organizational units in the Google Admin console
1.1. Why organizational units?
2. Organizational structure overview
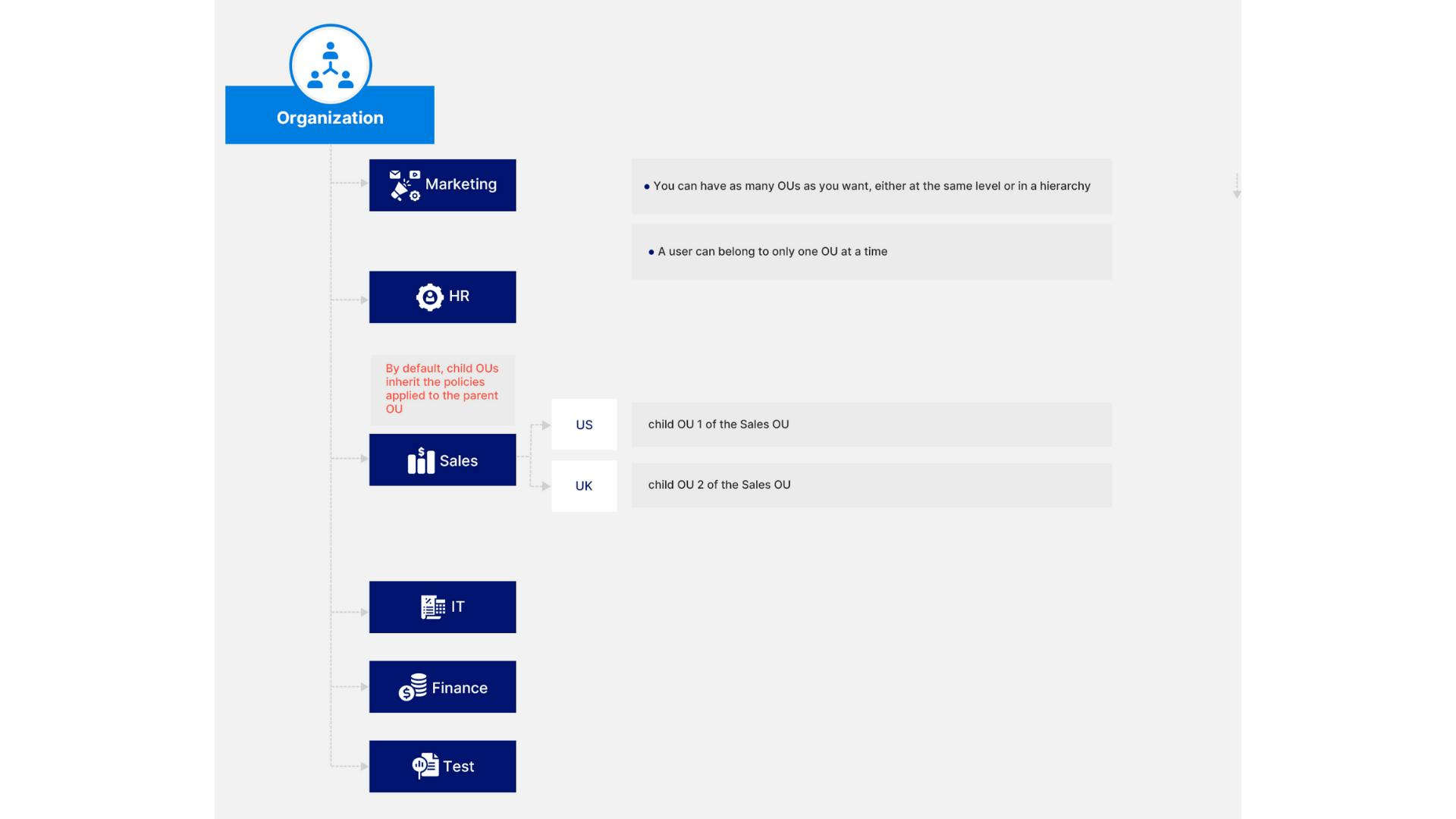
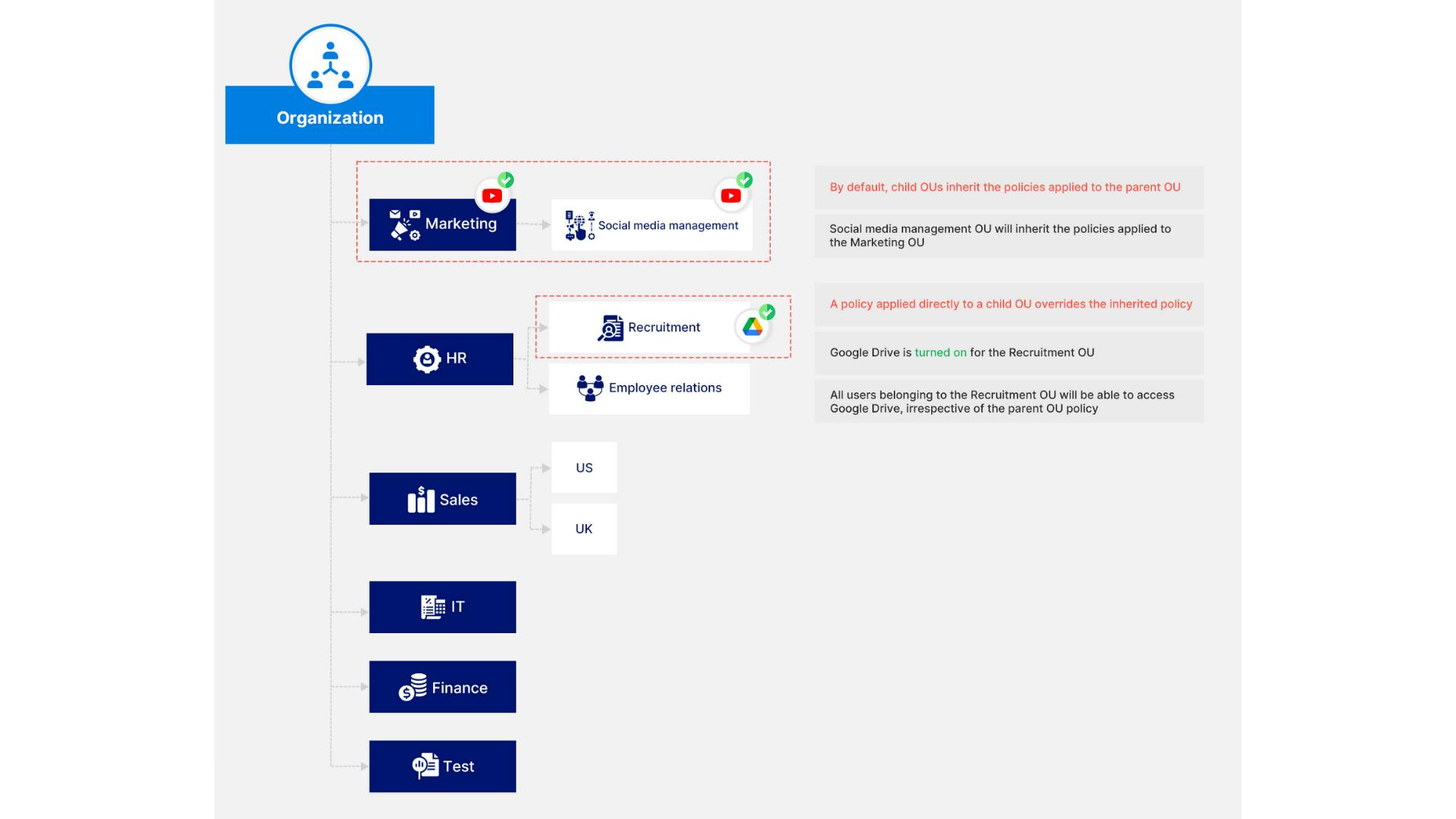
3. Building the organizational structure
3.1. Create a new organizational unit
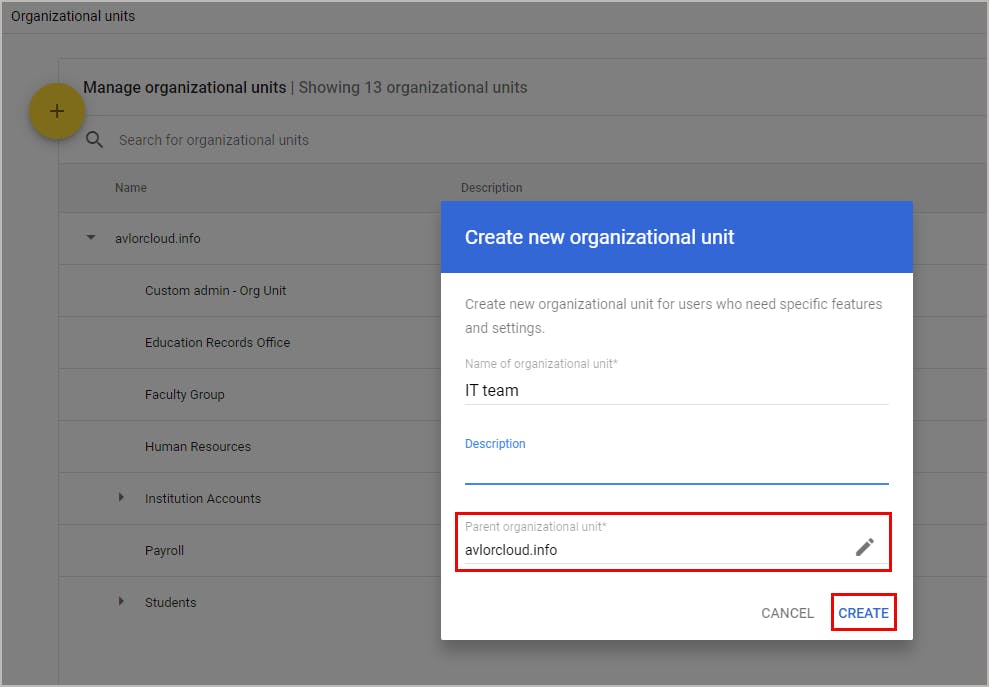
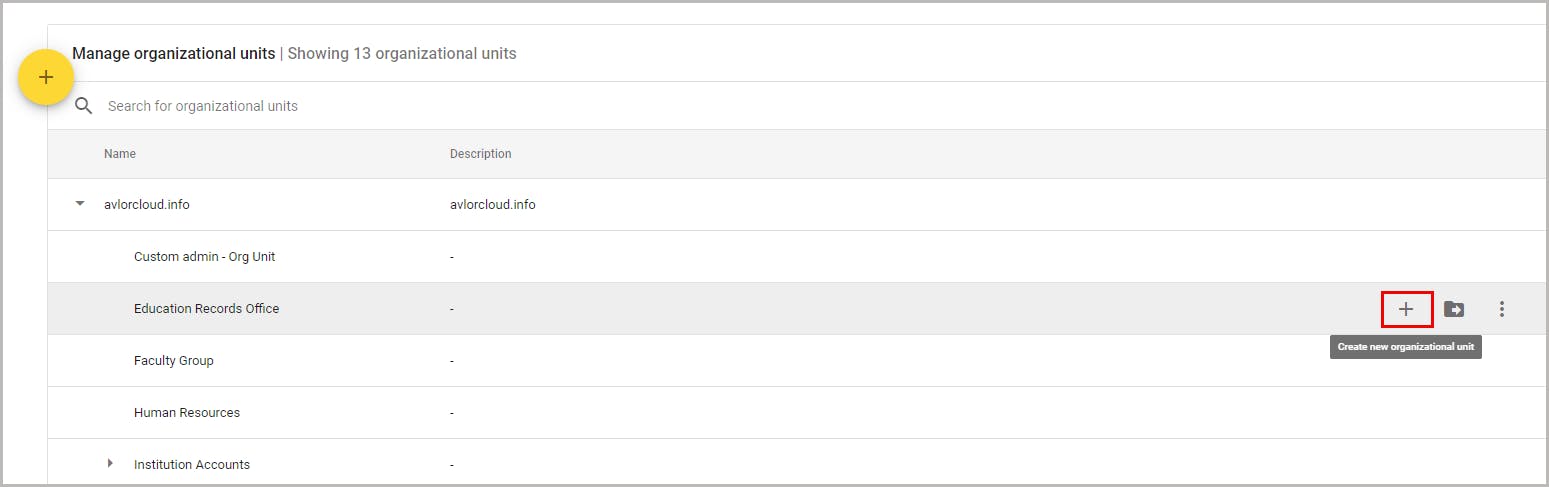
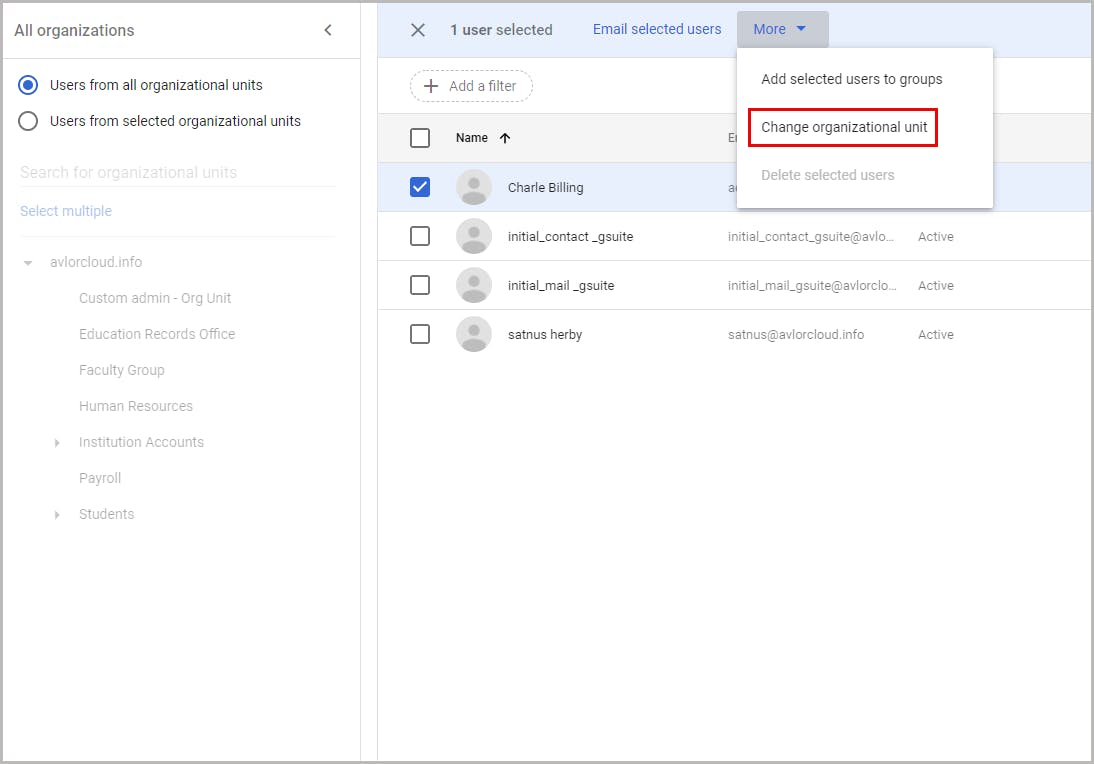
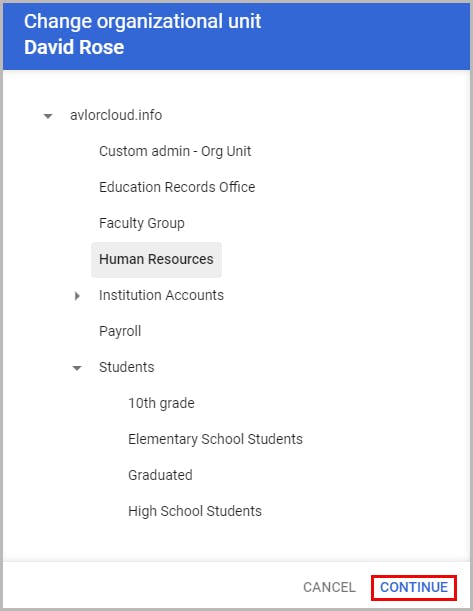
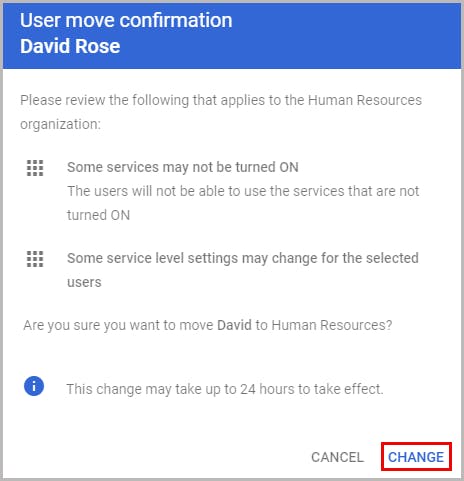
3.2. Move users to an organizational unit
3.3. Add a Chrome device to an organizational unit
4. Organizational units and permissions
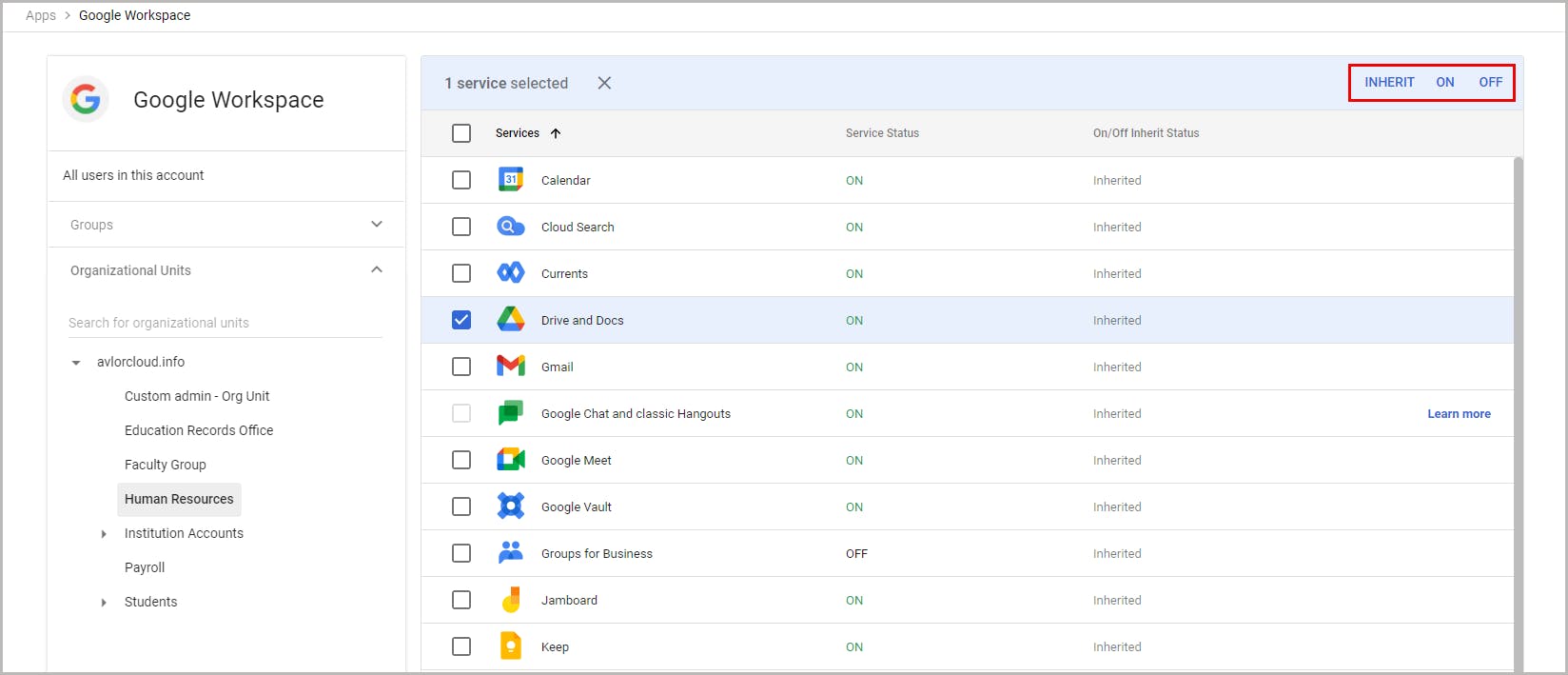
4.1. Turn app services on or off for users
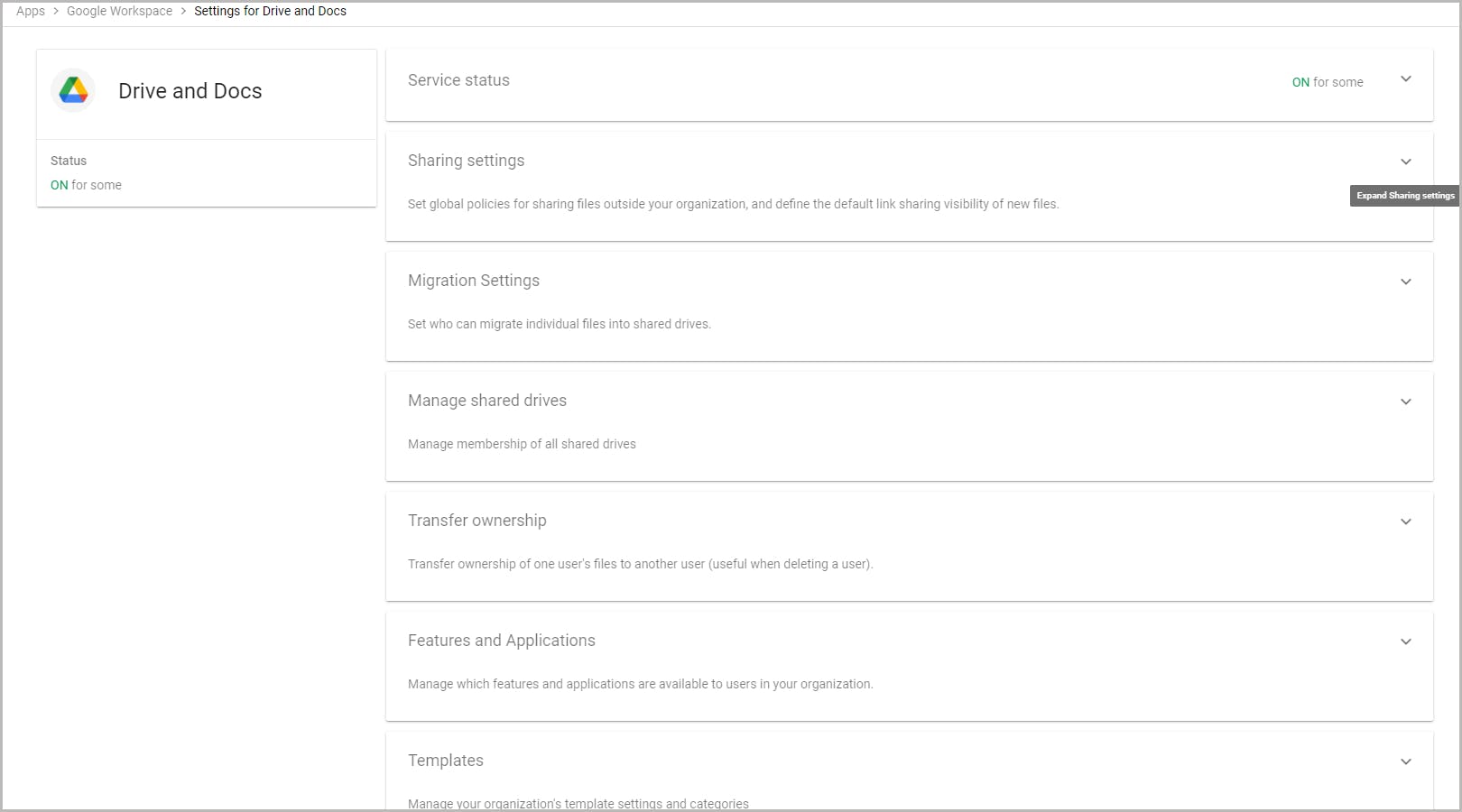
4.2. Change service settings for users
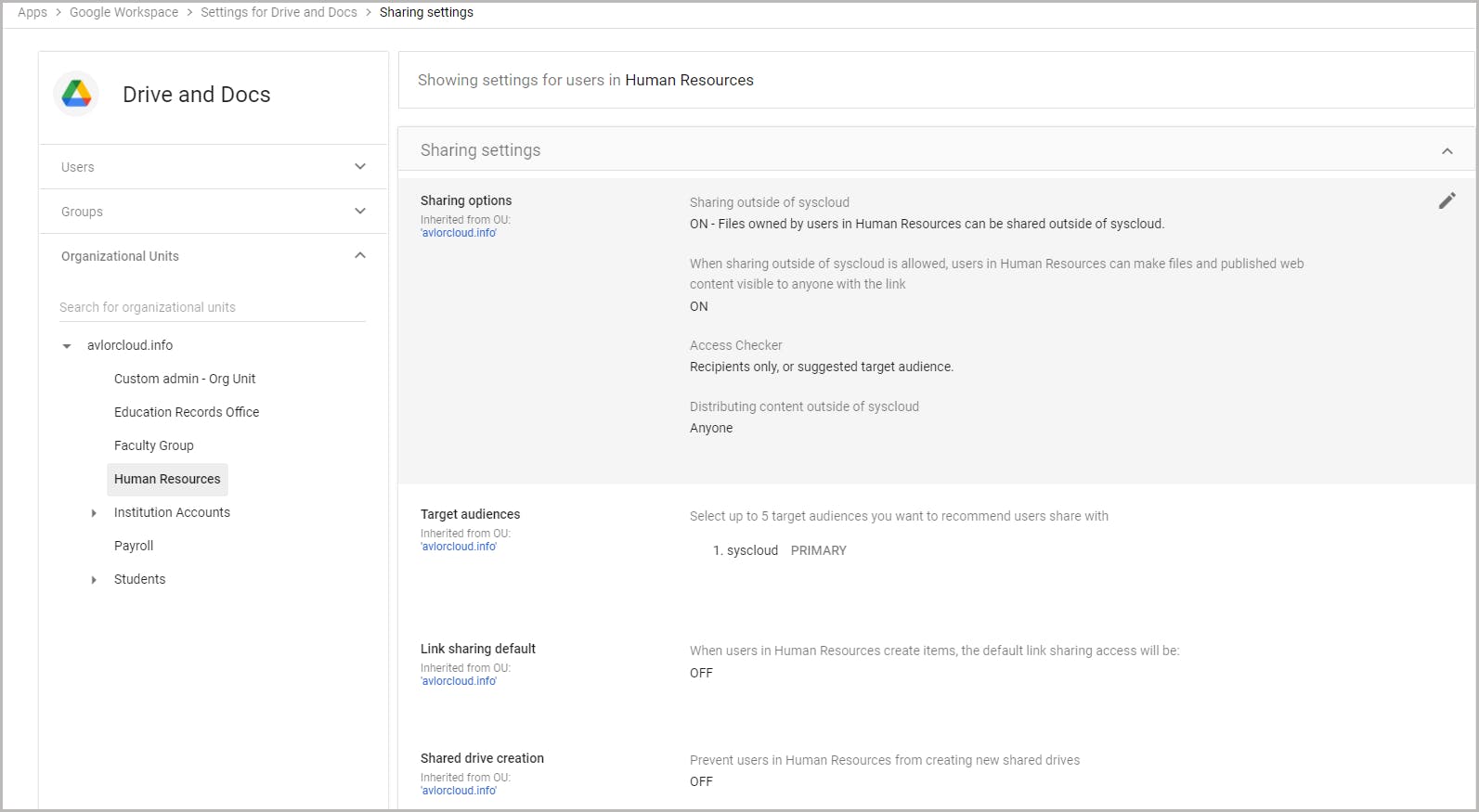
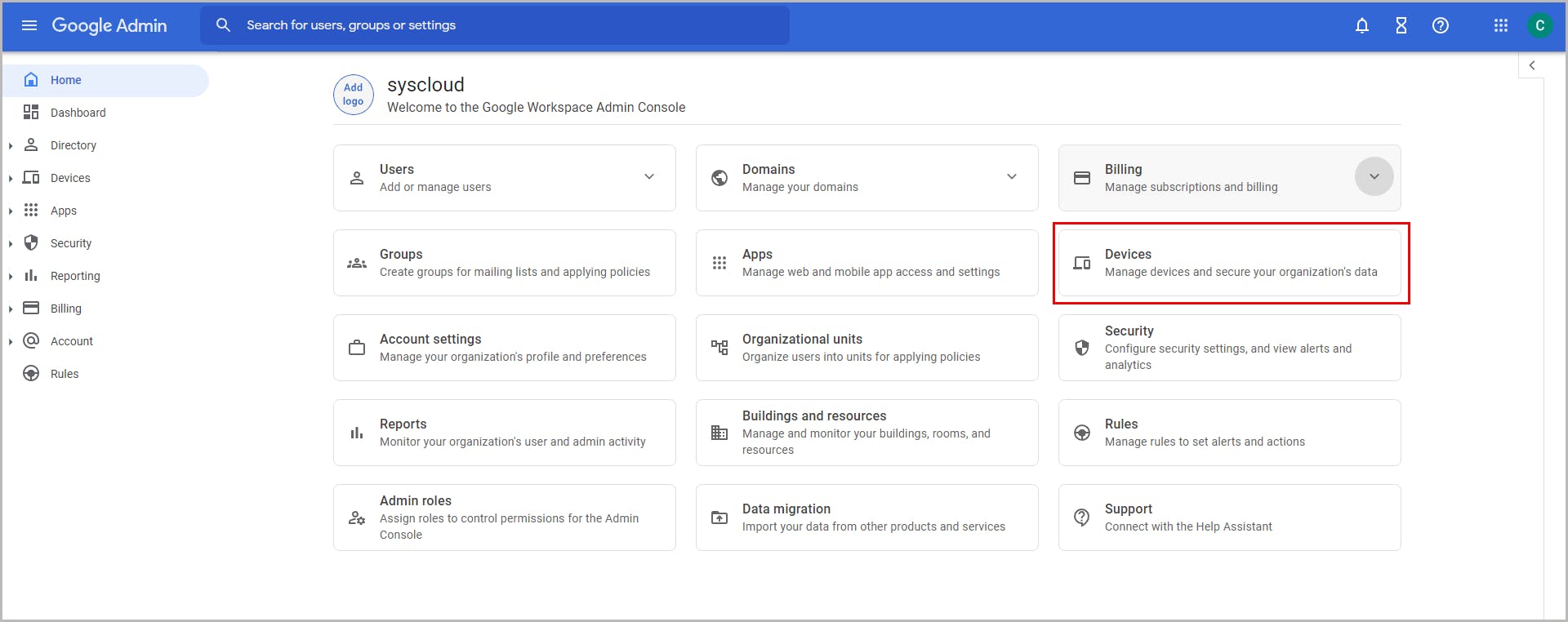
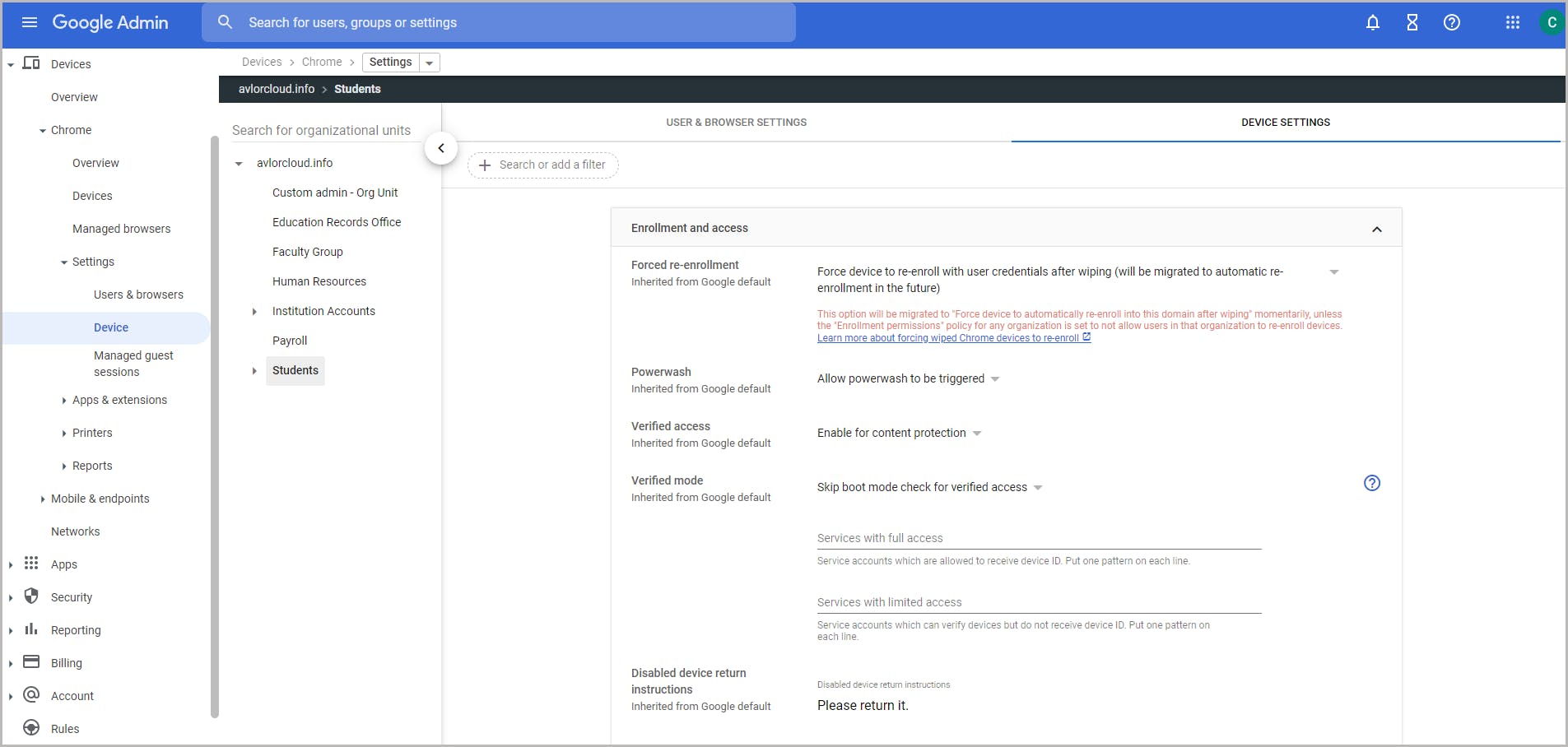
4.3. Change settings for Chrome devices
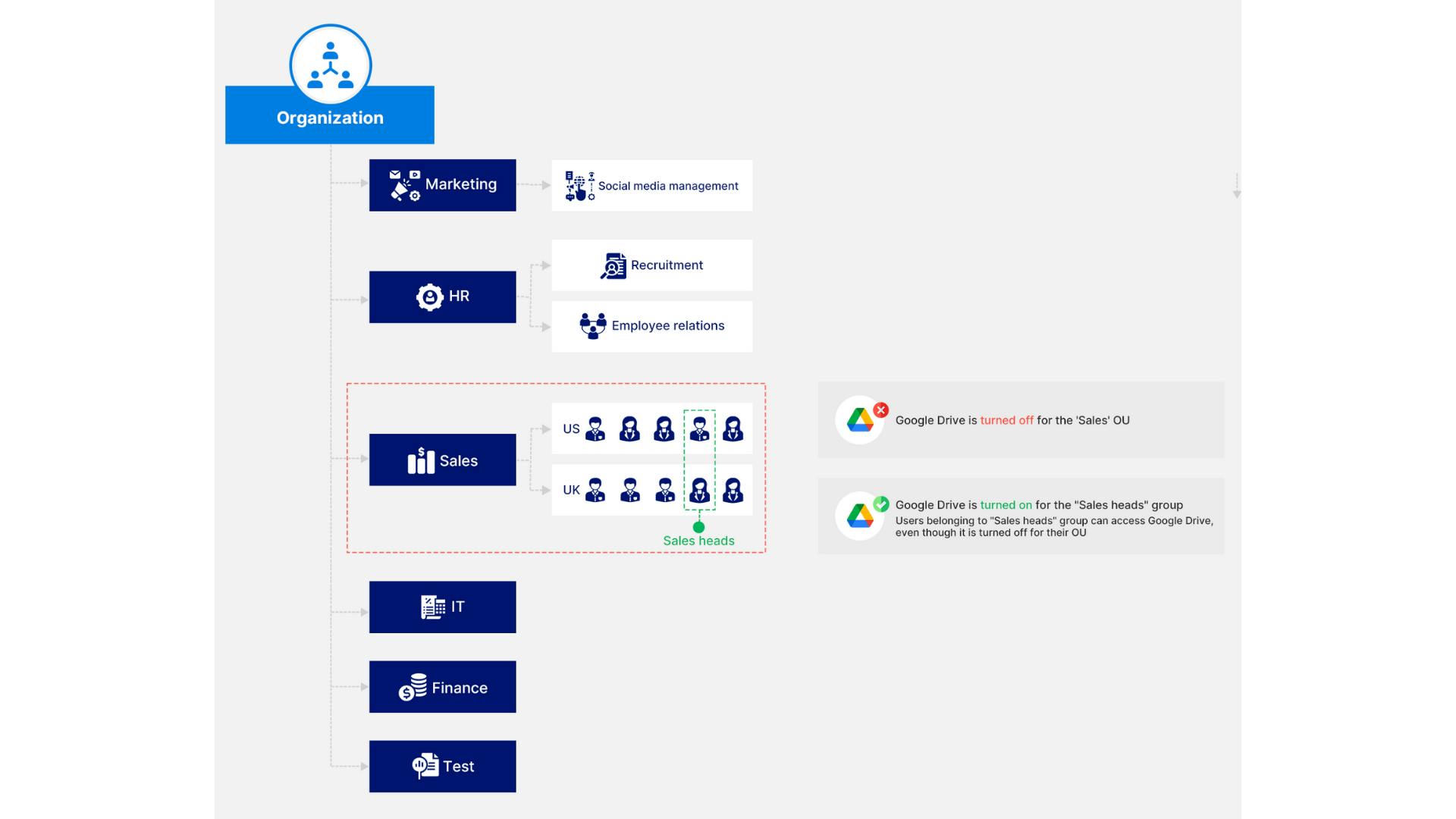
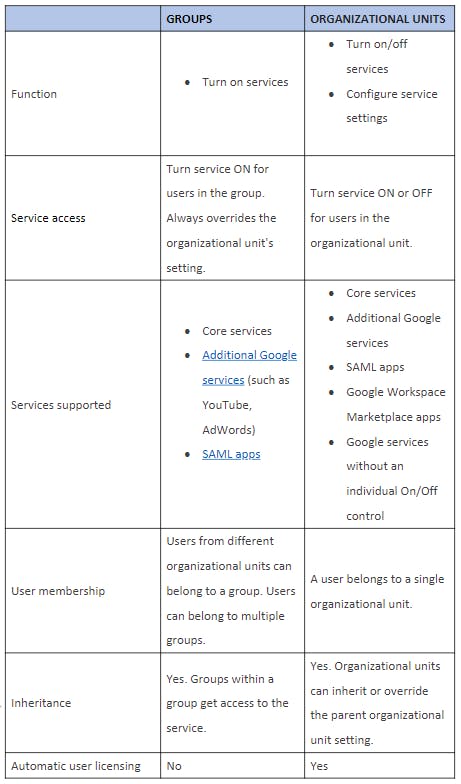
5. Google organizational units vs. access groups
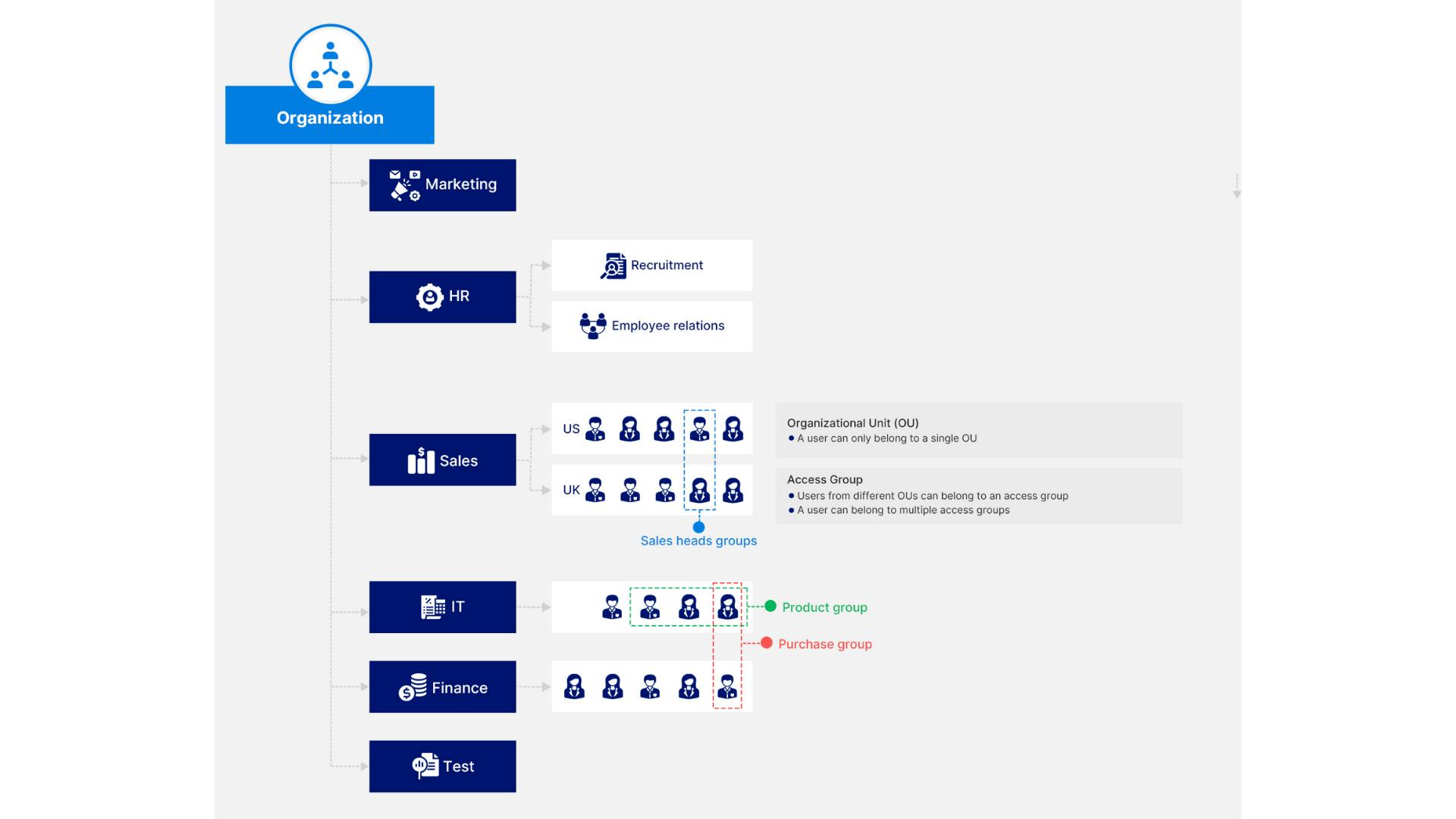
5.1. Customize service access using access groups
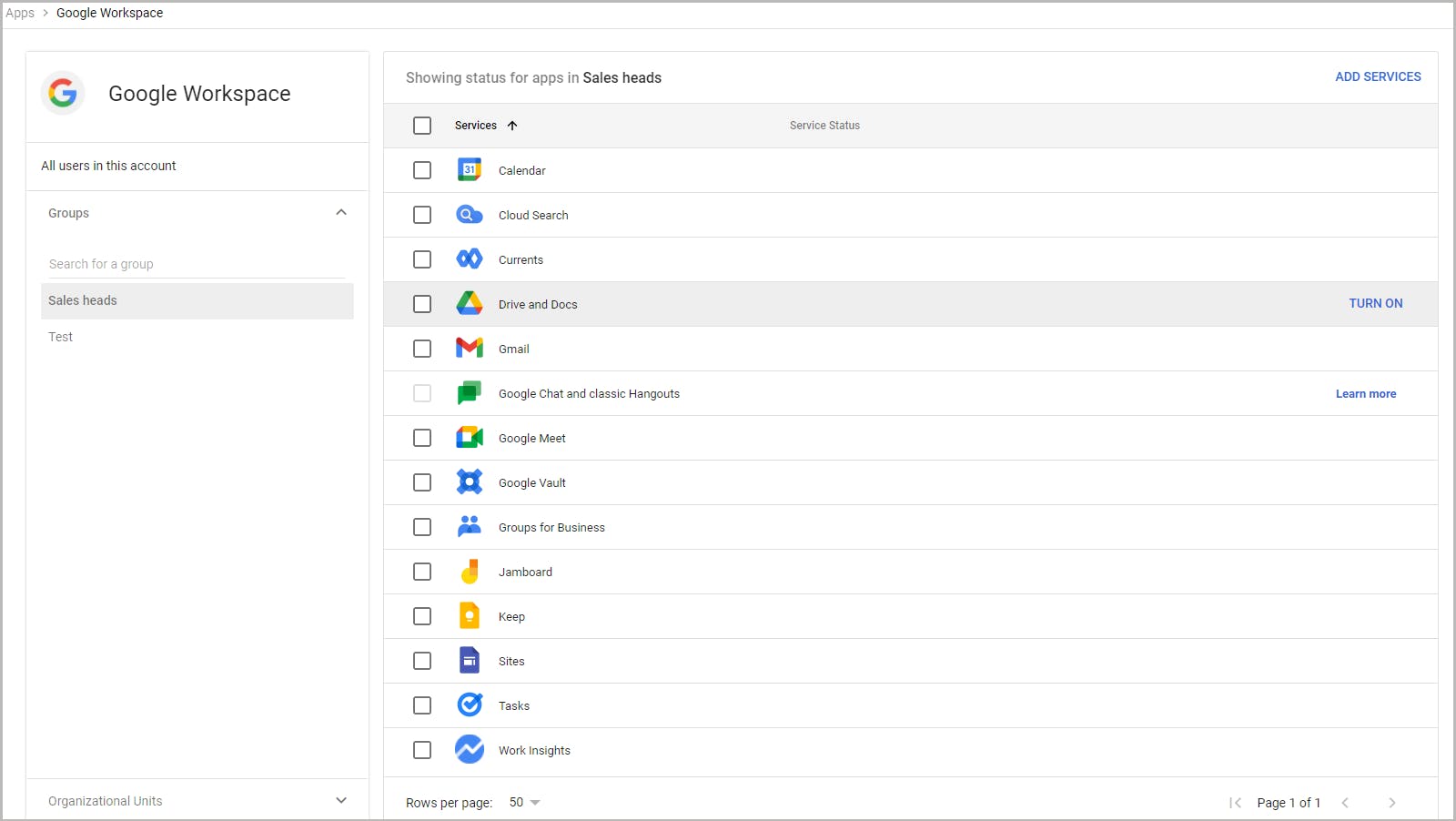
5.2. How to create an access group
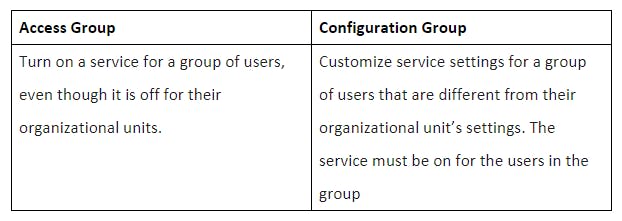
5.3. Customize service settings using configuration groups
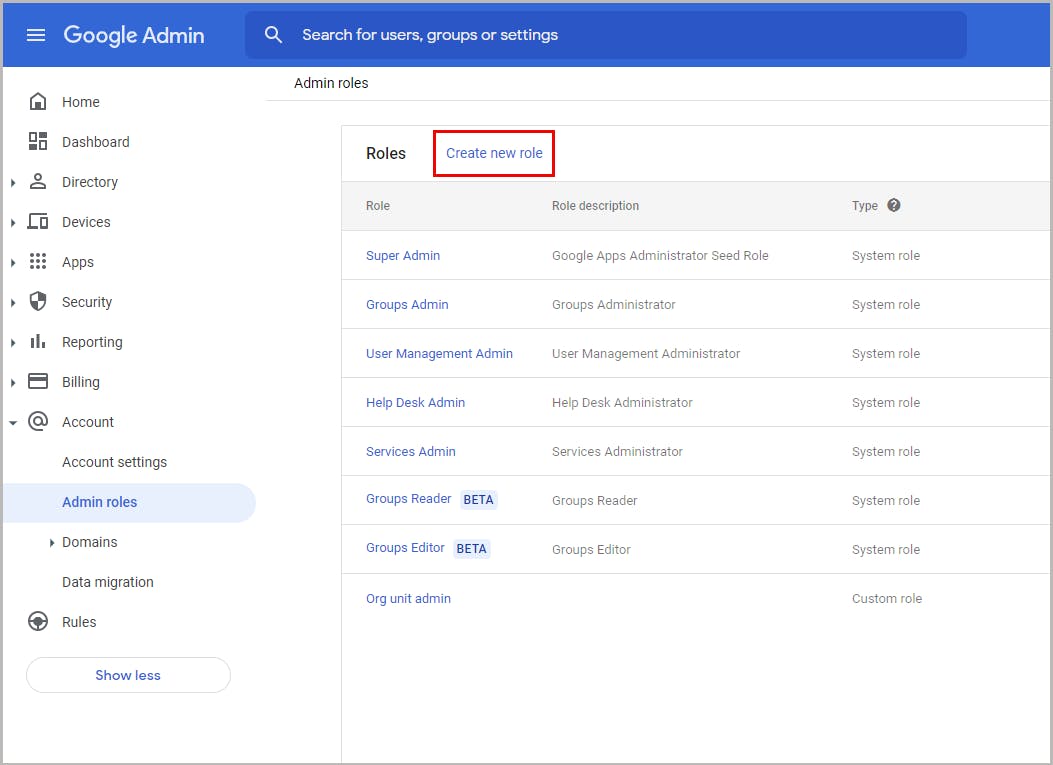
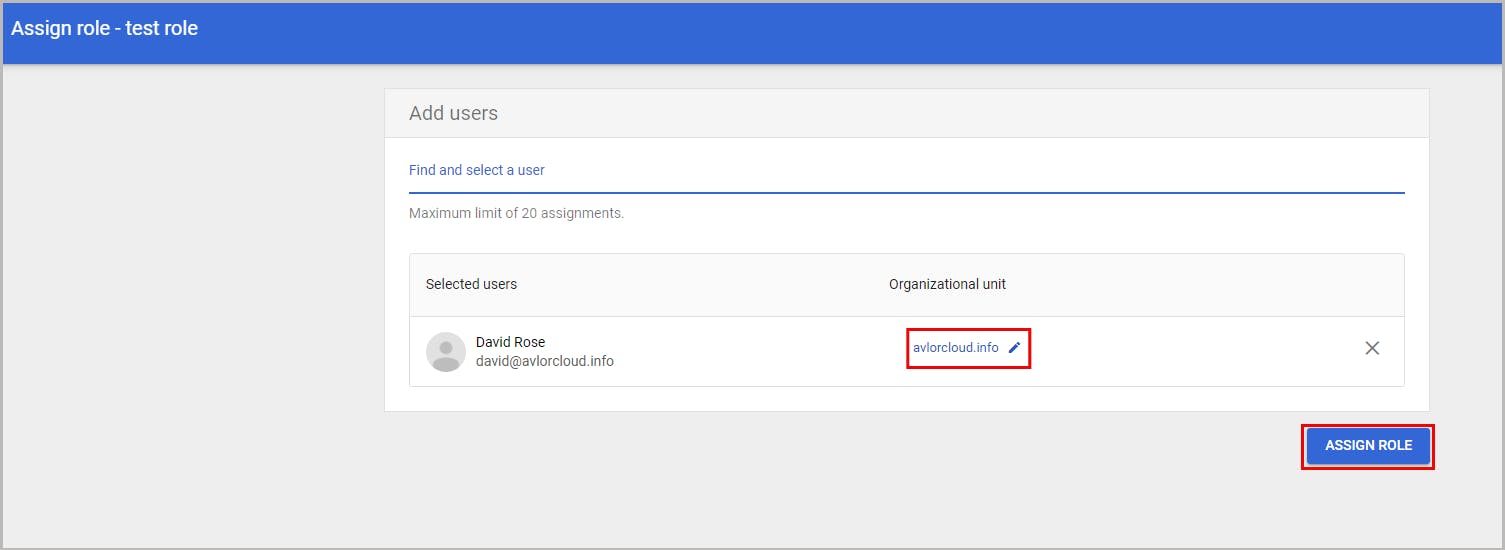
6. Admin role for an organizational unit
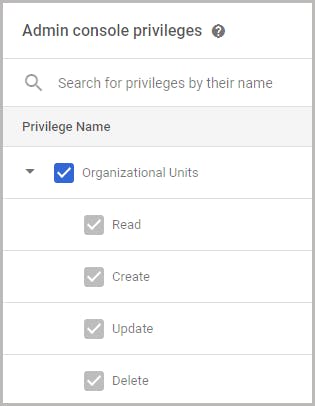
6.1. Administrator privileges required
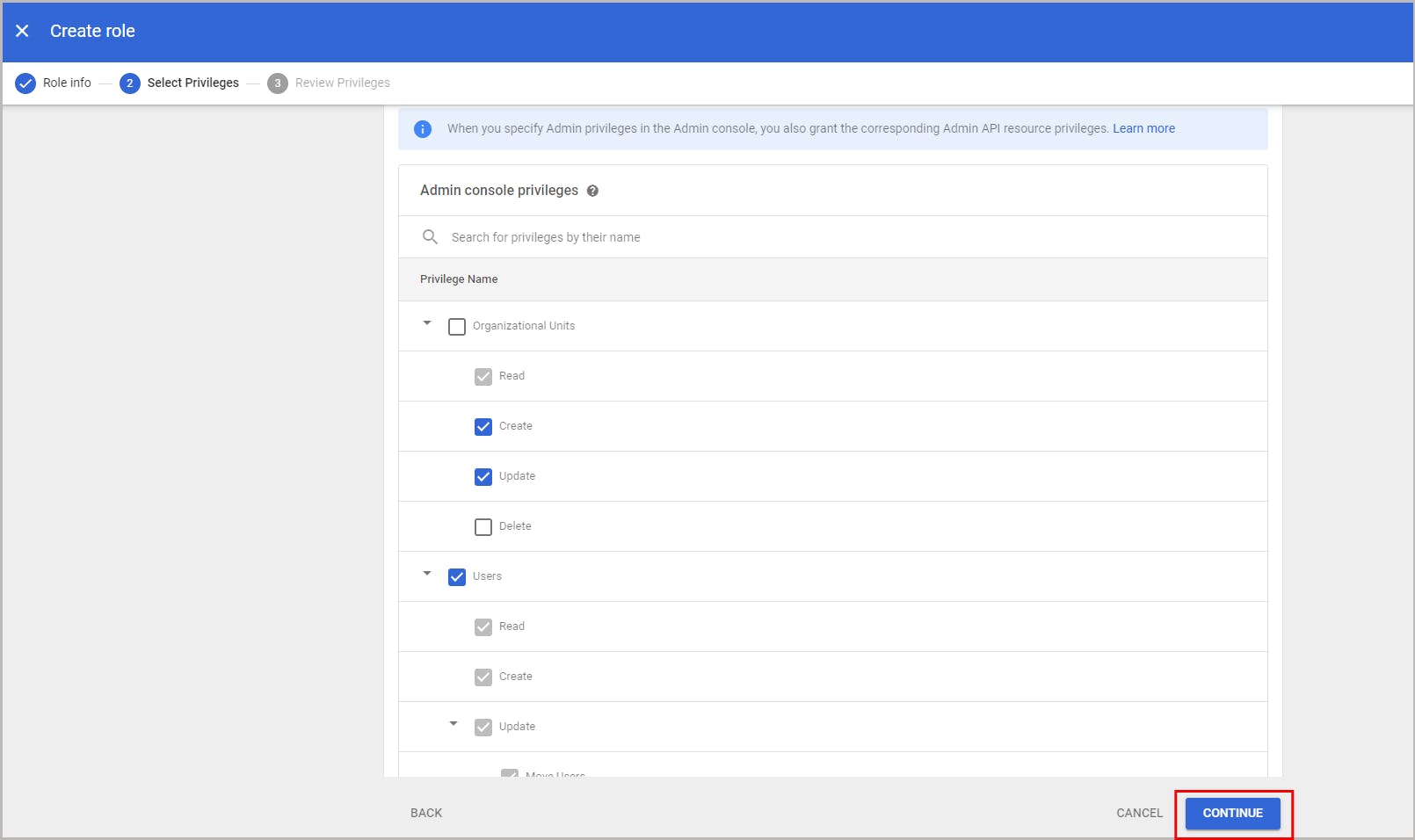
6.2. How to create a custom administrator role for an organizational unit
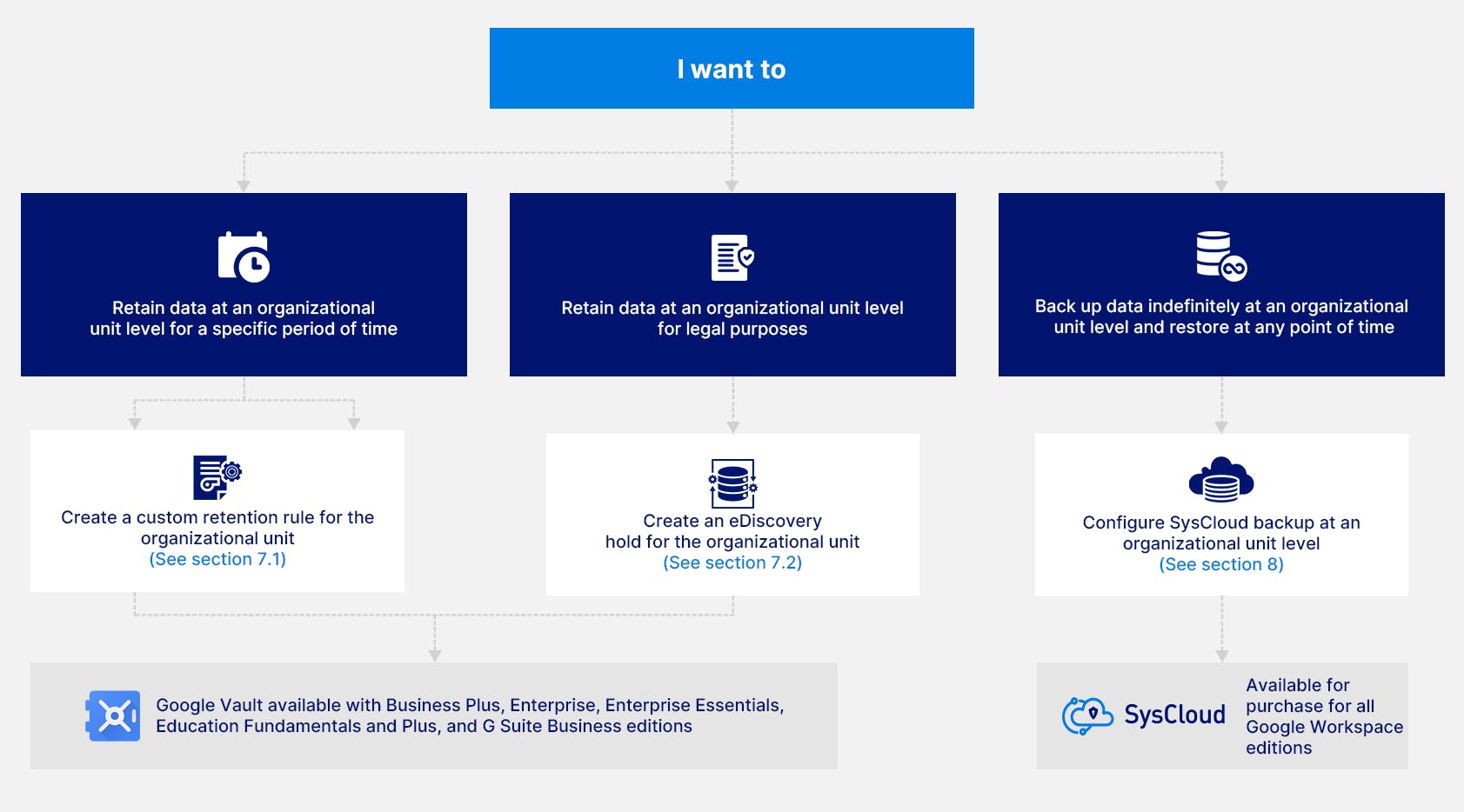
7. Data retention management for Google organizational units
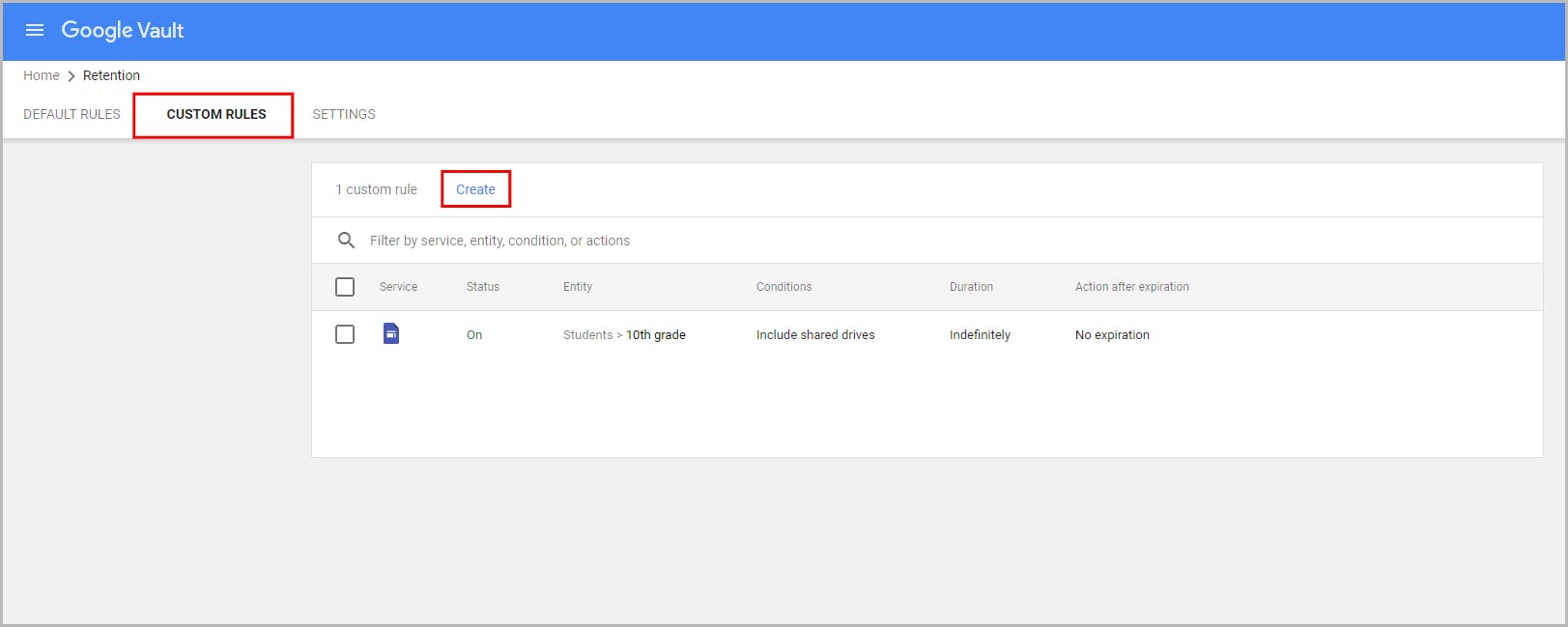
7.1. Retain data at an organizational unit level using retention rules
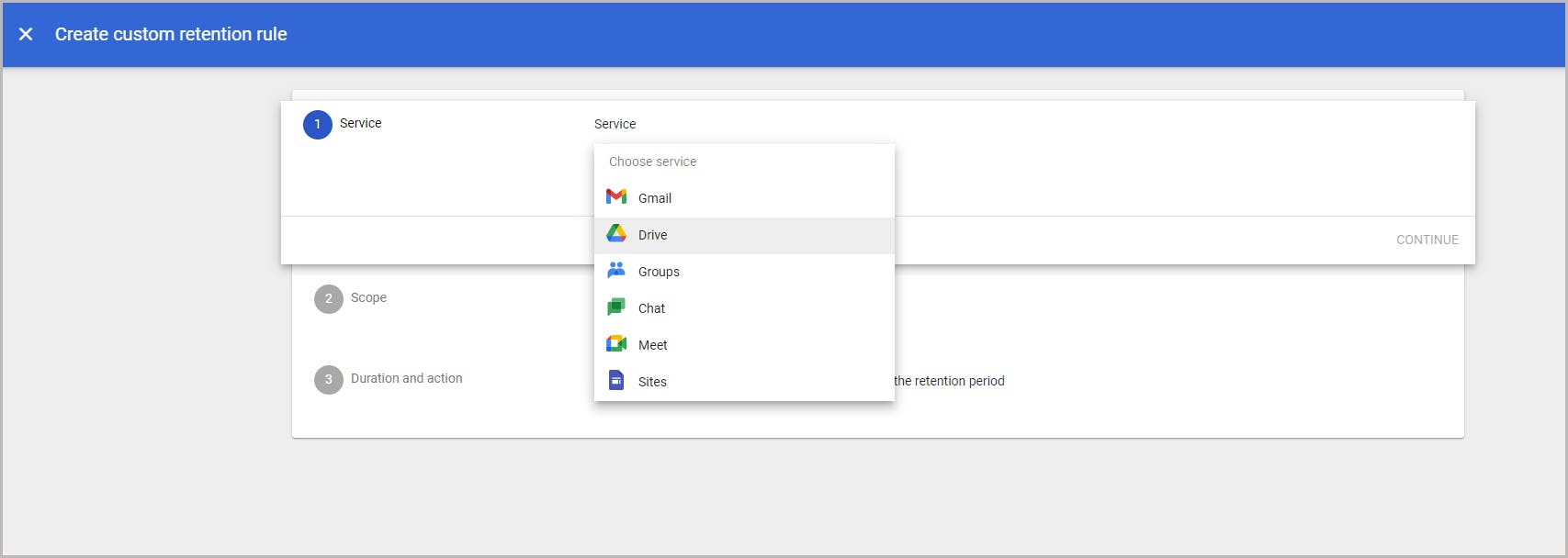
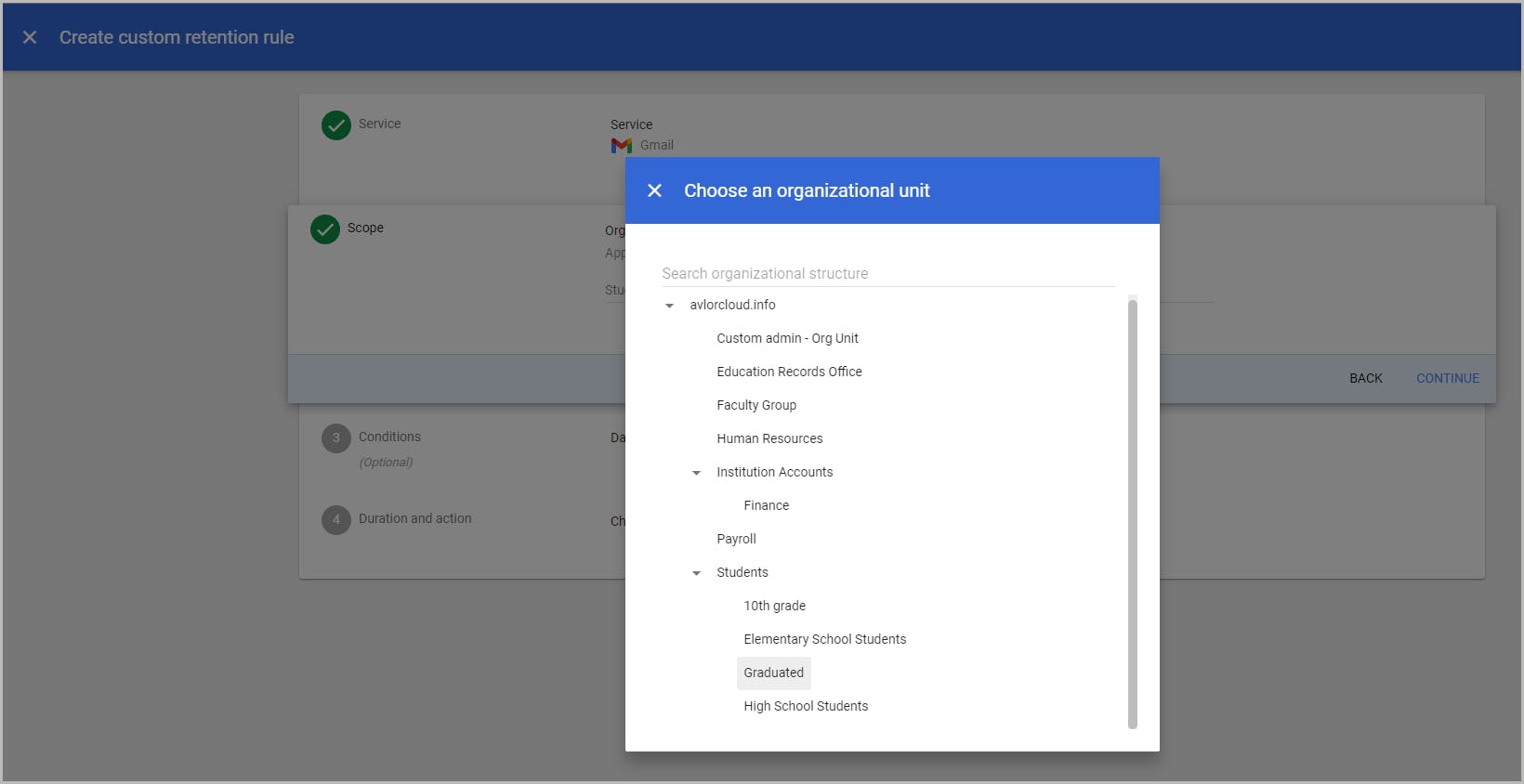
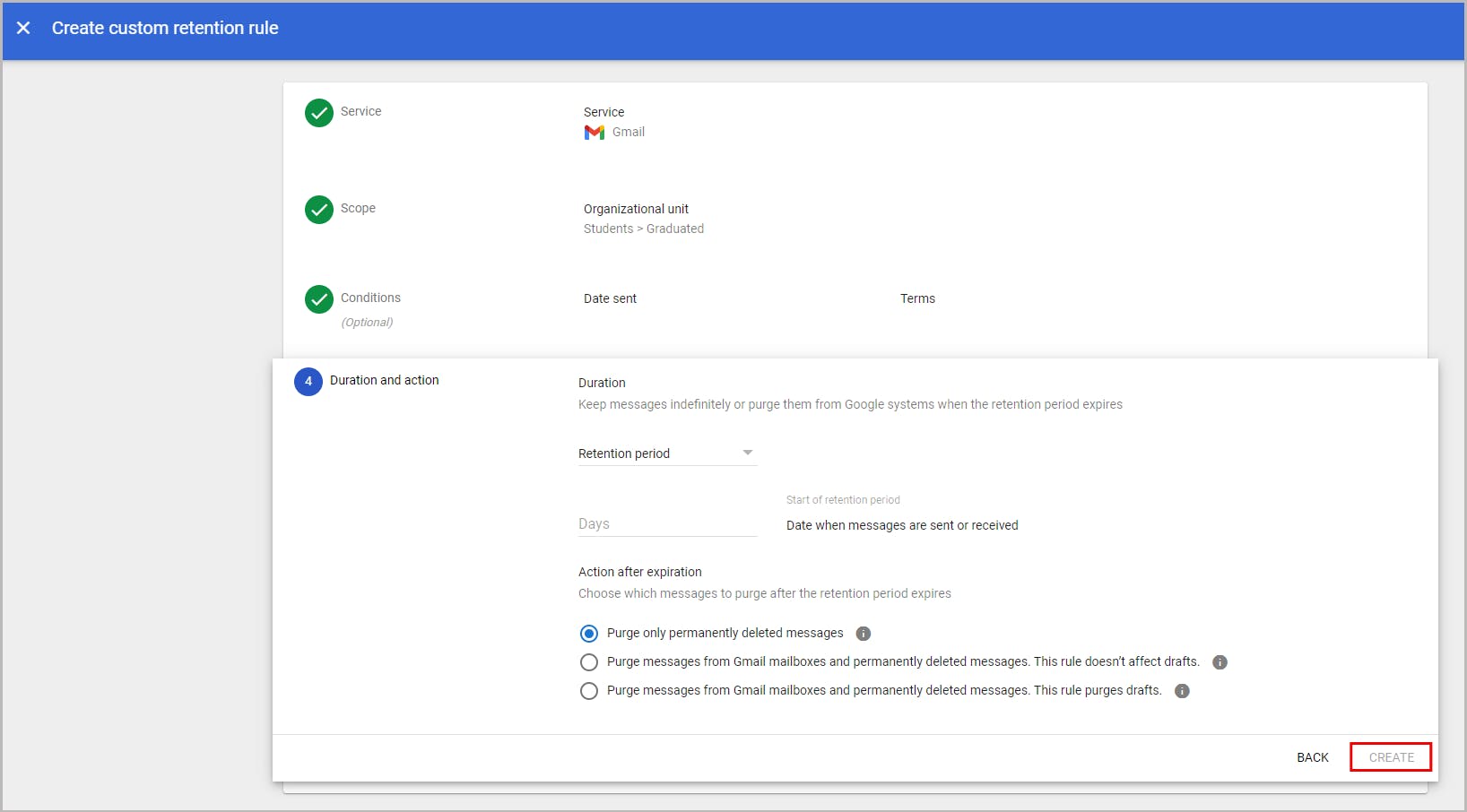
7.2. Retain data at an organizational unit level using holds
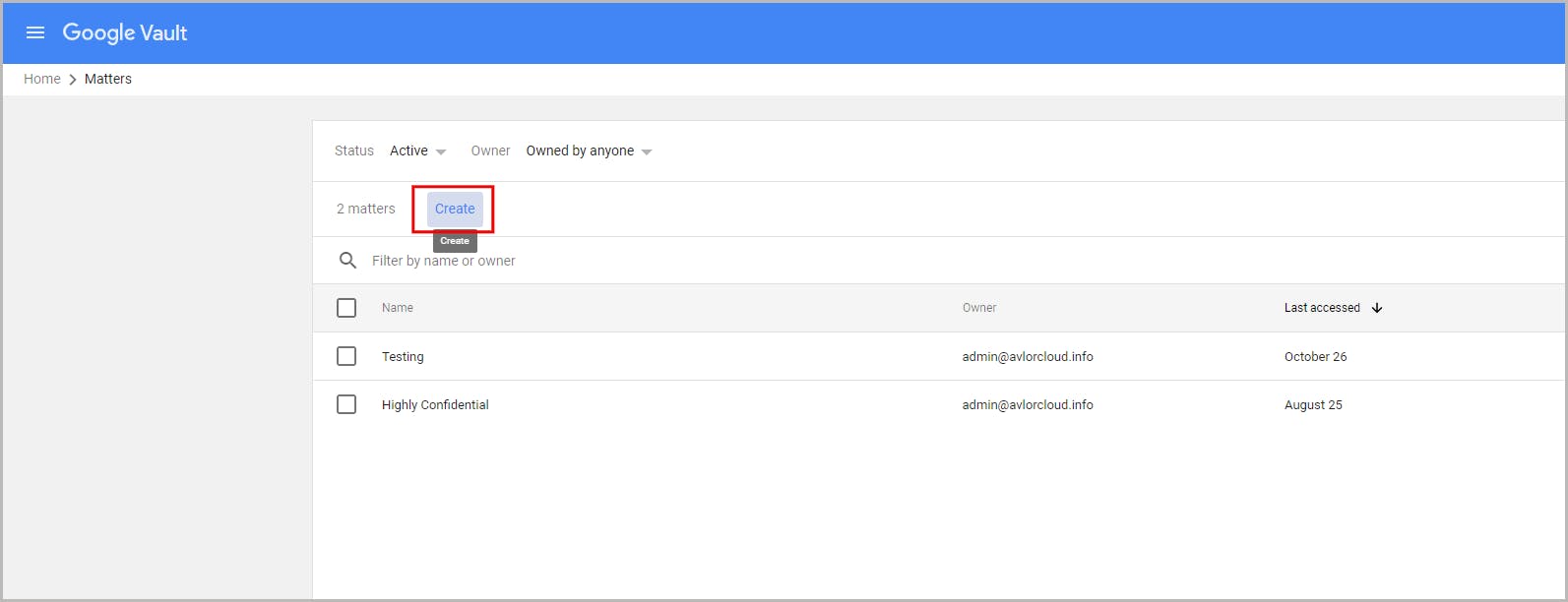
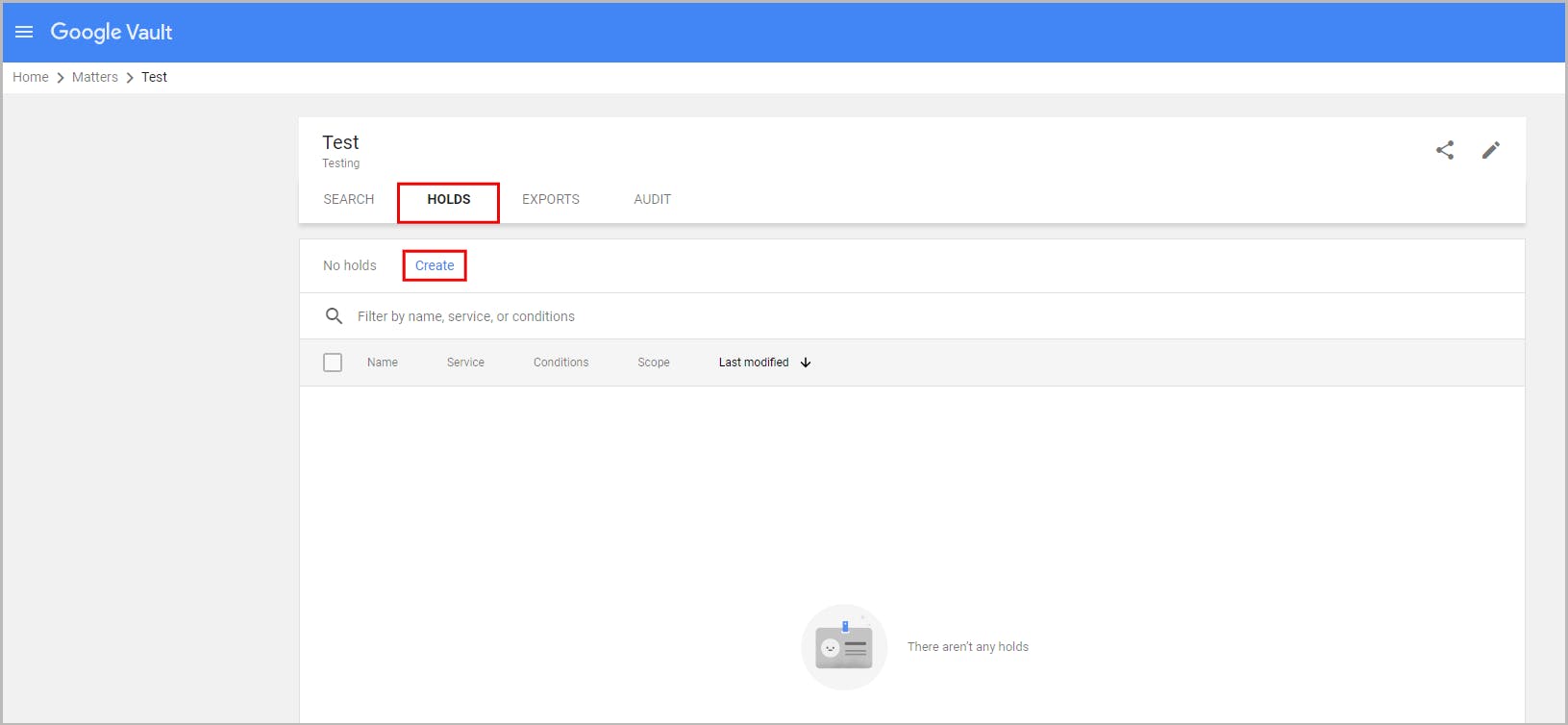
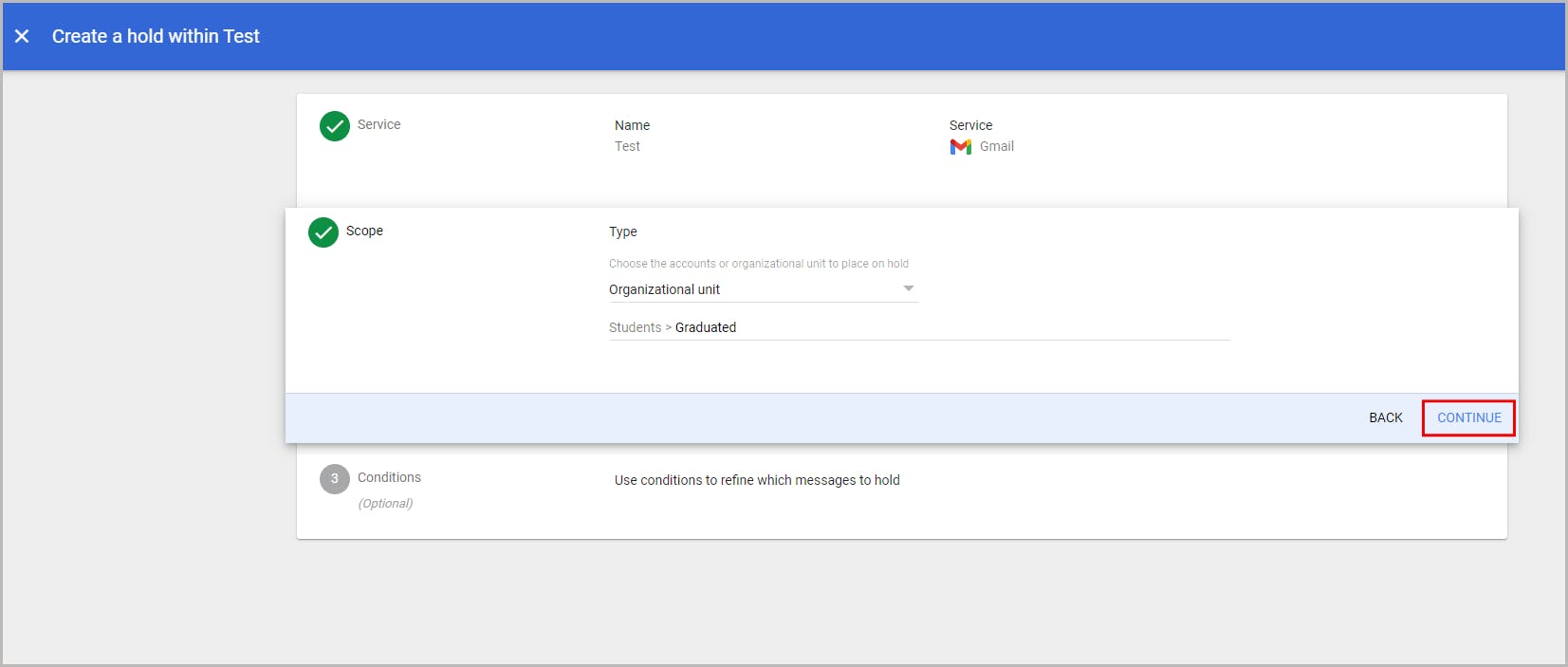
7.3. Limitations of using retention rules and holds as a backup solution
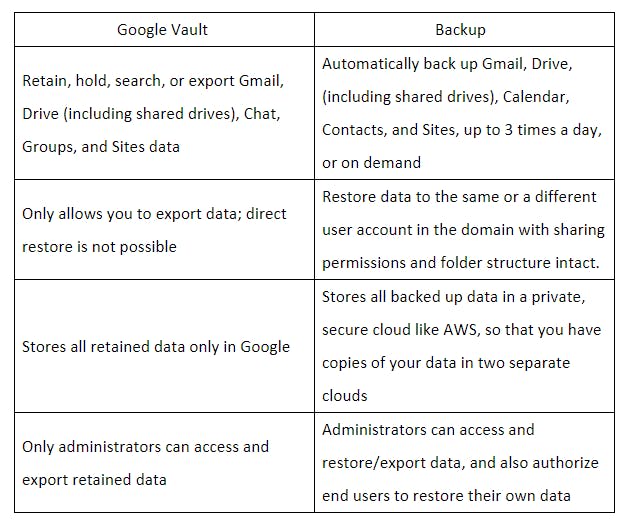
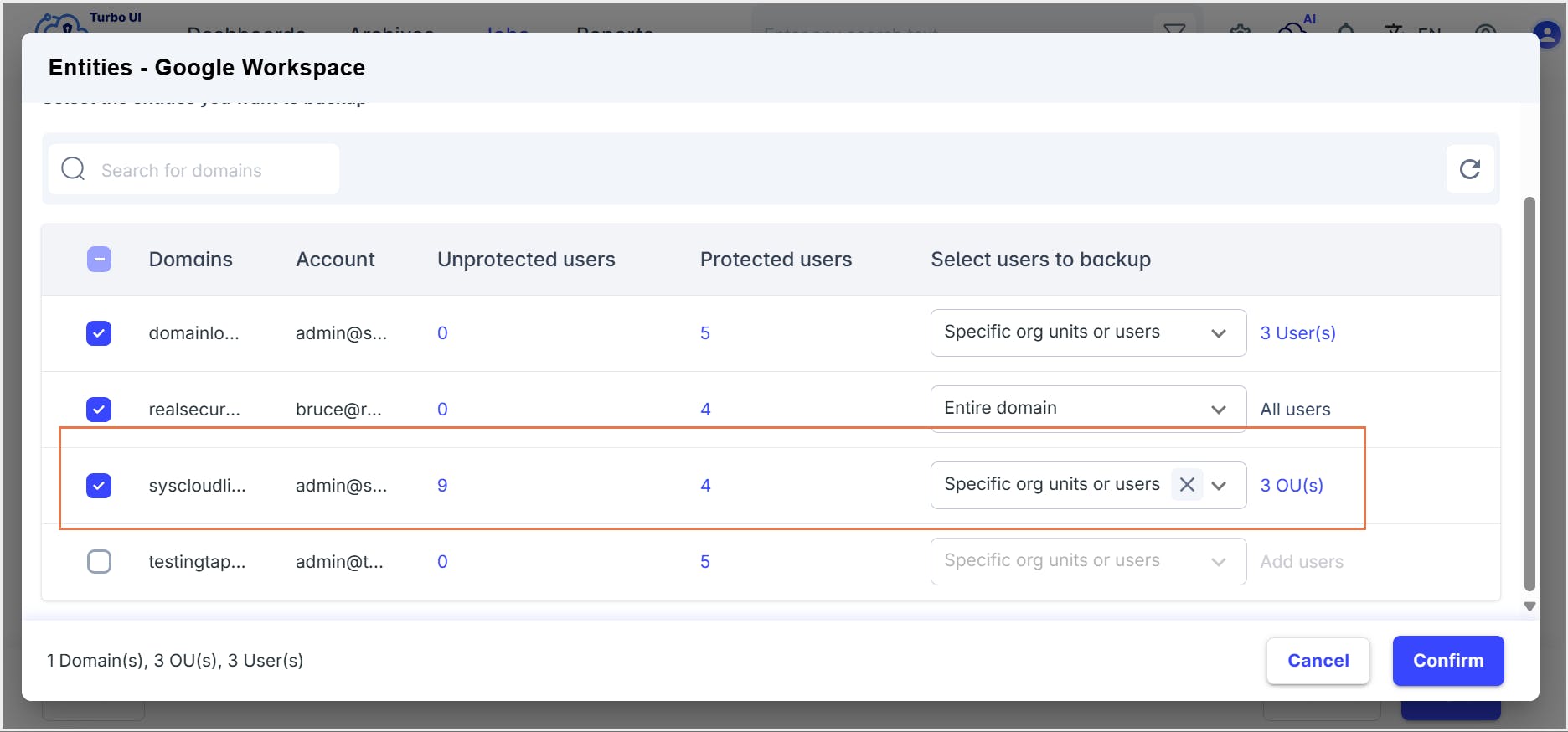
8. SysCloud backup for Google Workspace