In this article
- What Is Brand Impersonation?
- How Can Brands Protect Themselves and Their Customers?
Blog Articles
Article at a glance
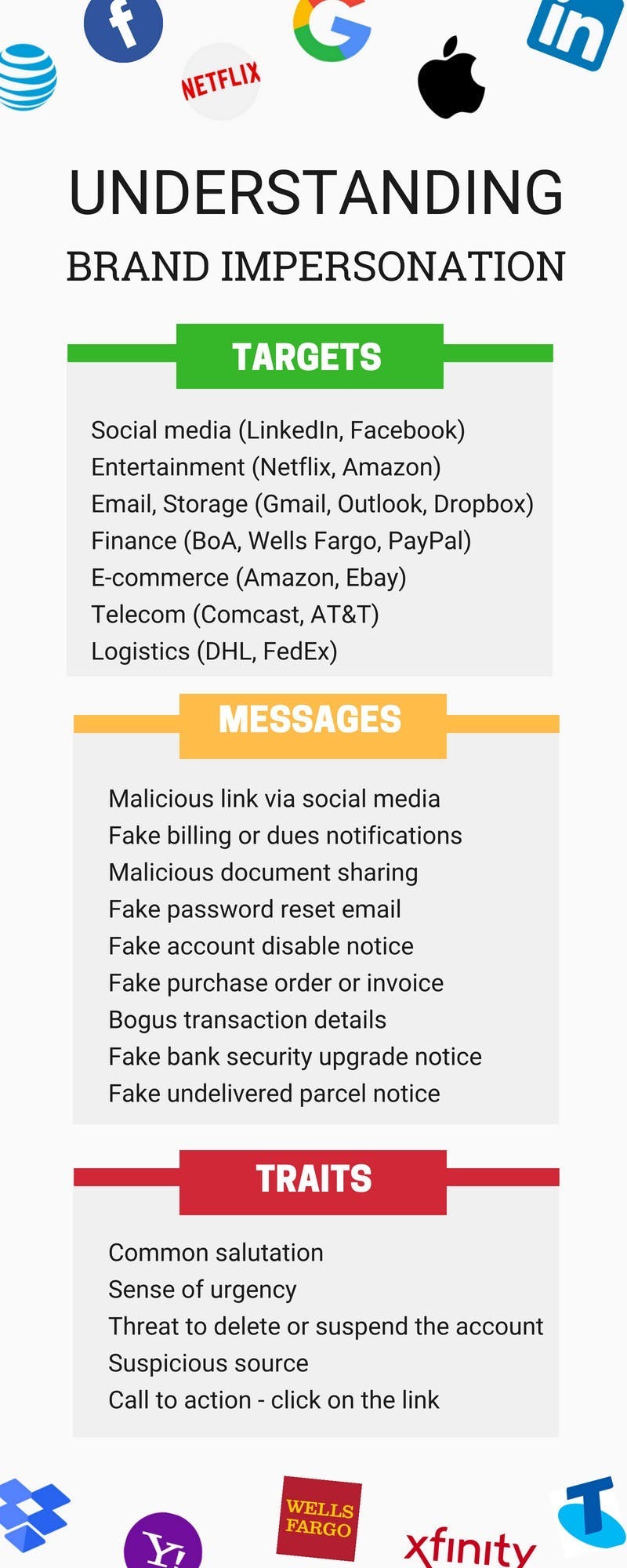
Brand impersonation attacks target well-known brands to deceive users and steal data.
•Educate employees and customers about recognizing and reporting brand impersonation attempts.
• Use advanced security measures to detect and prevent brand impersonation attacks.
• SysCloud offers robust backup and data protection solutions (for example, ransomware detection) to protect against brand impersonation, ensuring all data is securely backed up and easily recoverable in case of an attack.
Read more

What is brand impersonation?
What are the motives of a hacker?
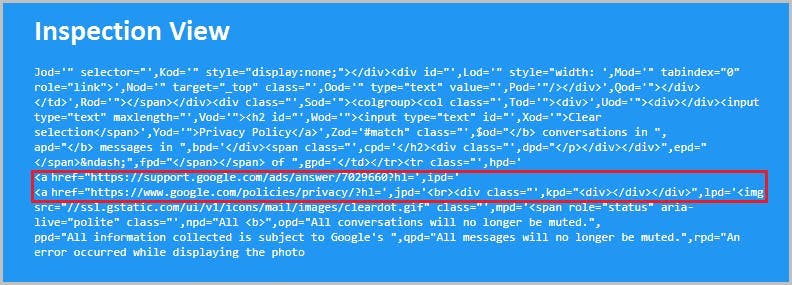
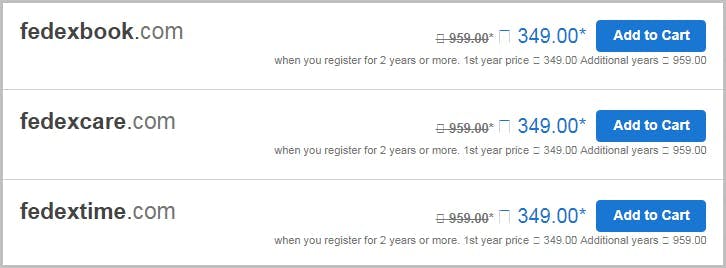
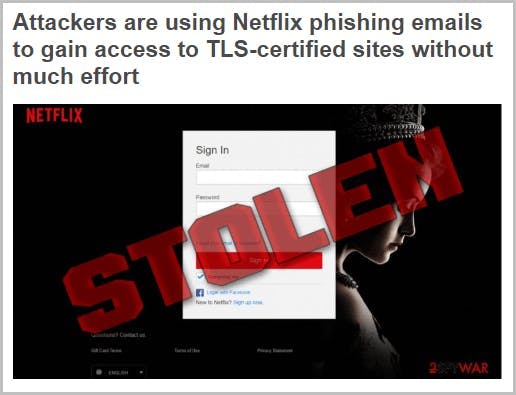
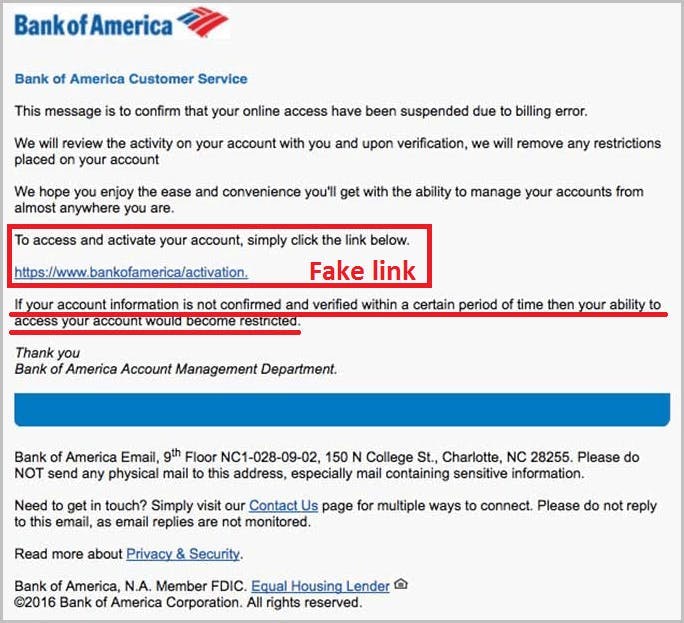
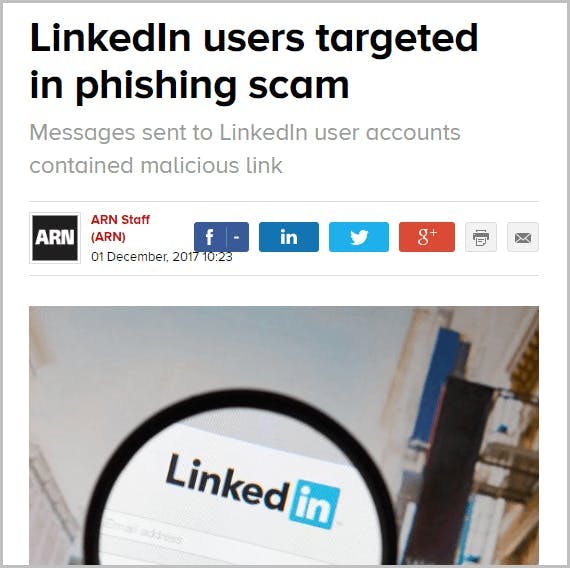
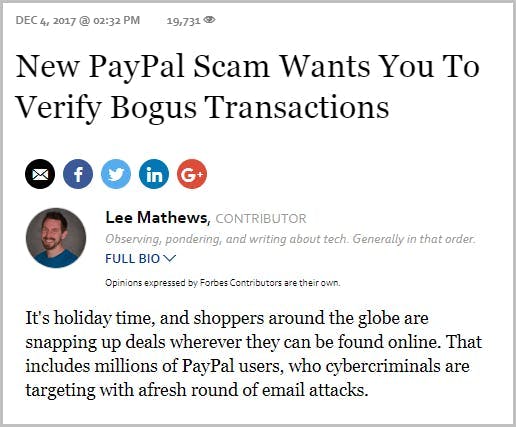
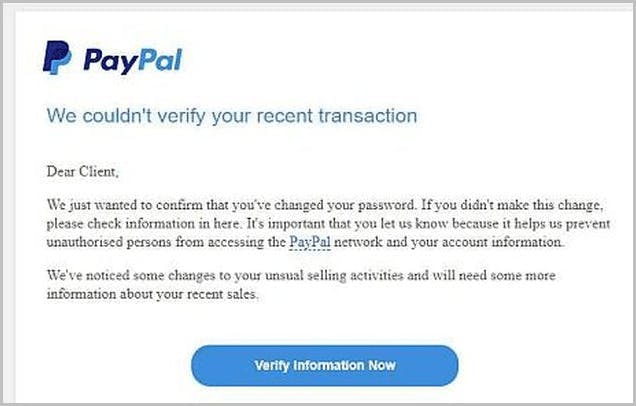
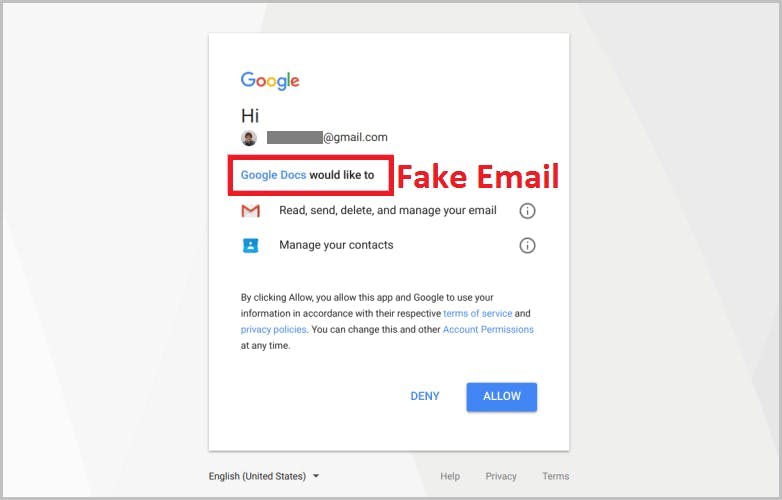
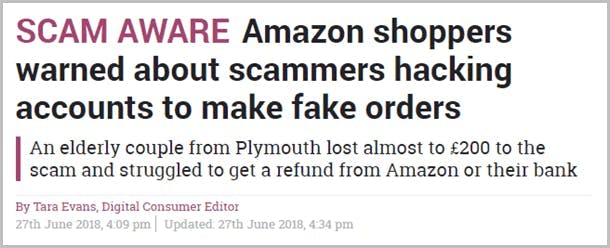
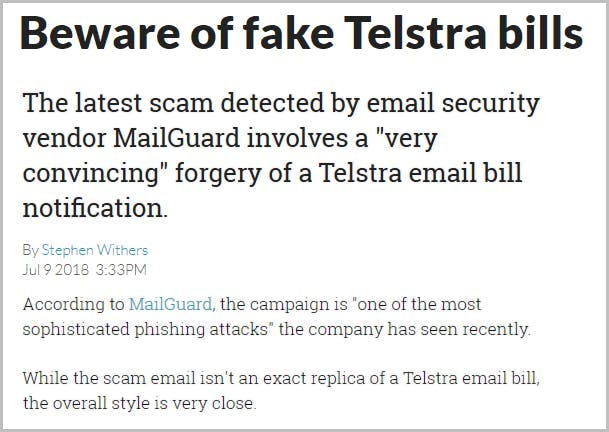
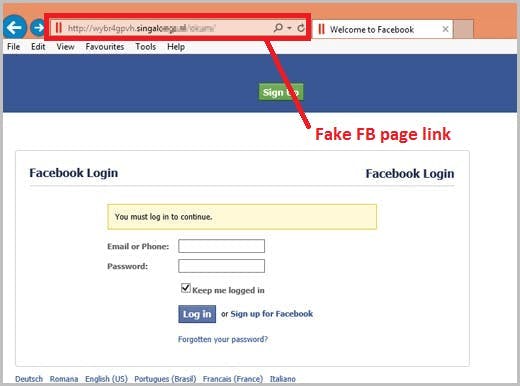
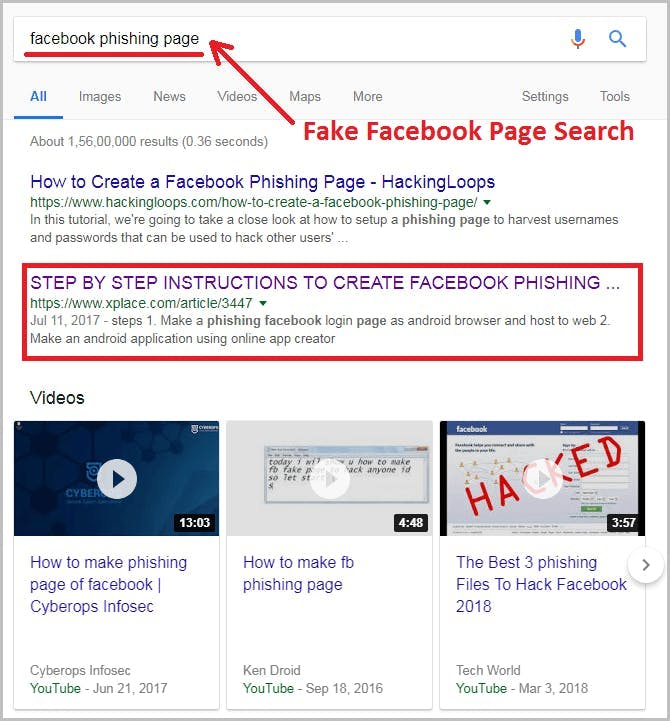
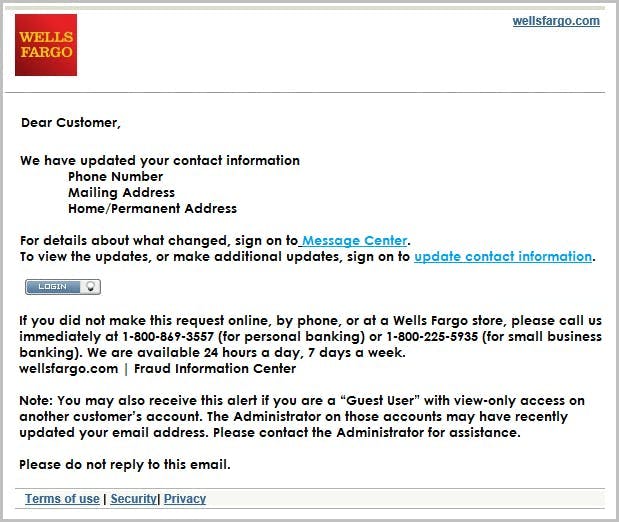
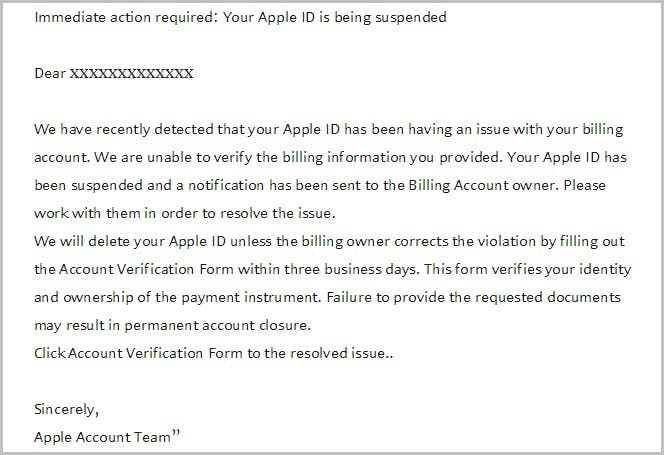
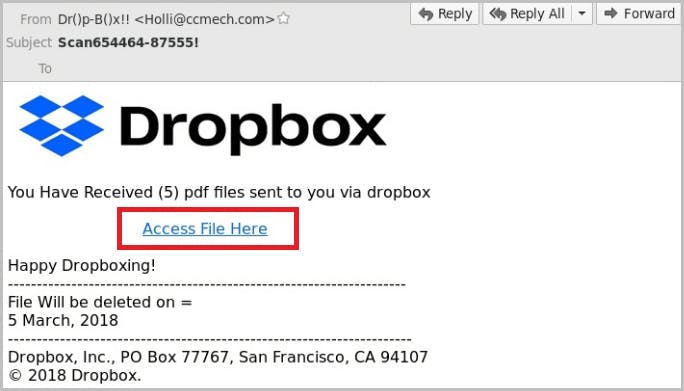
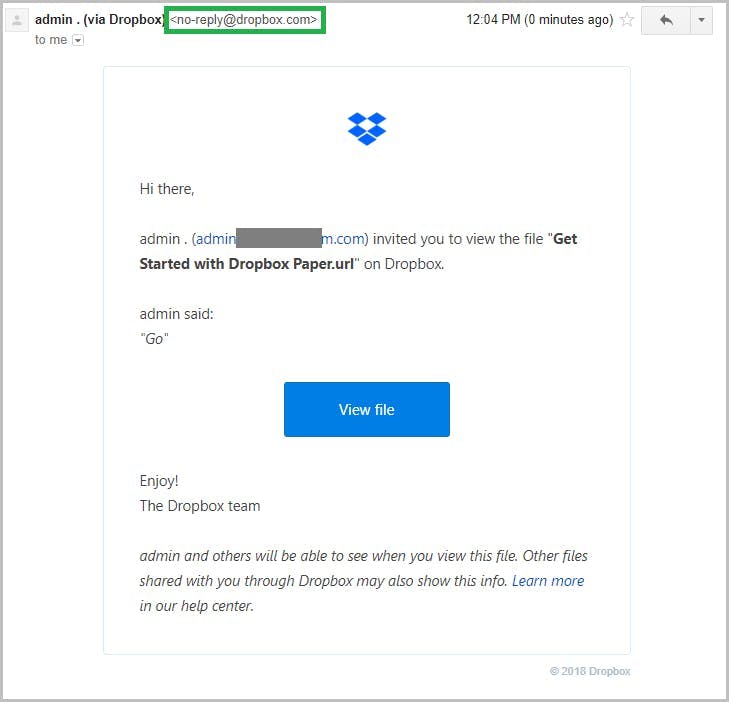
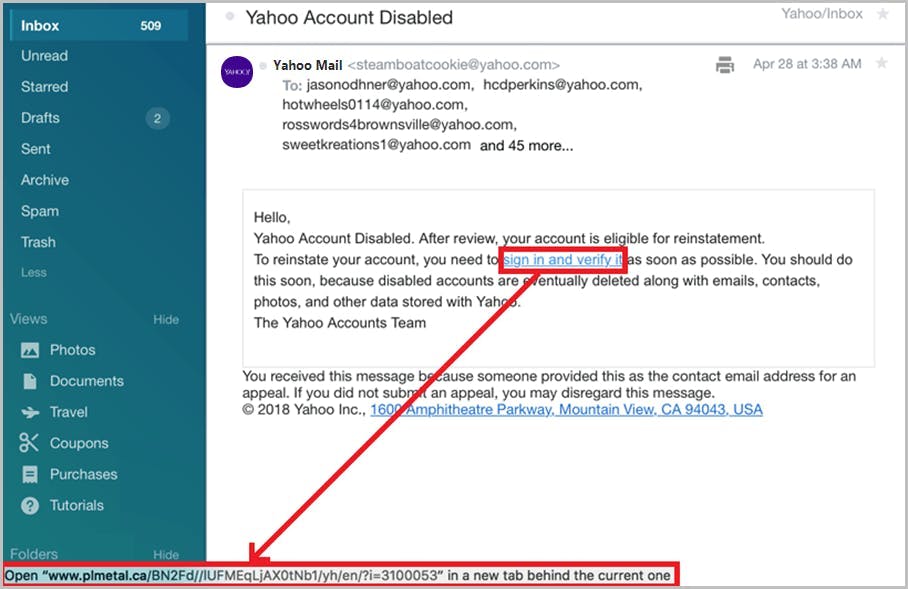
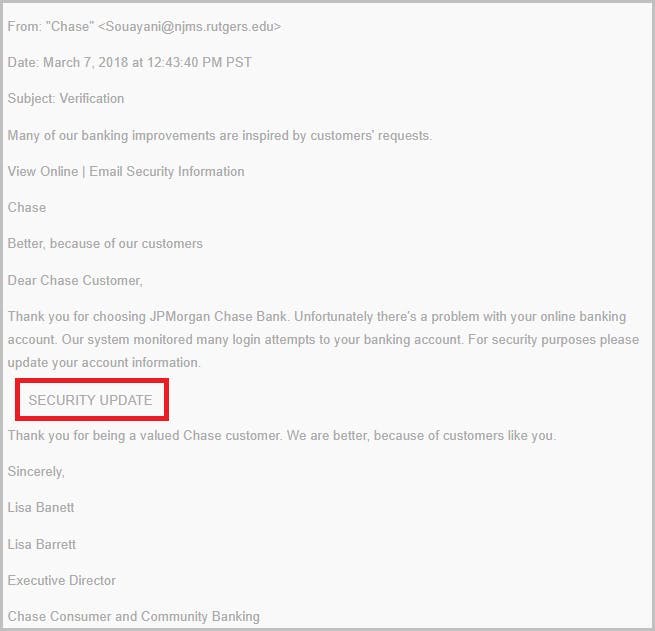
How do hackers impersonate a brand?

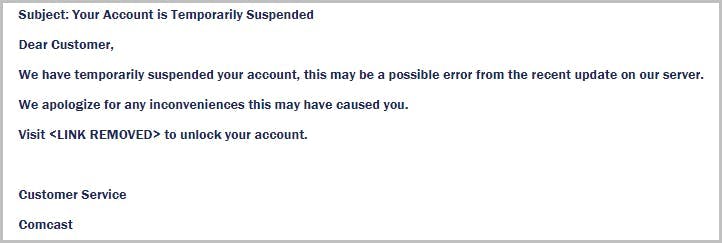
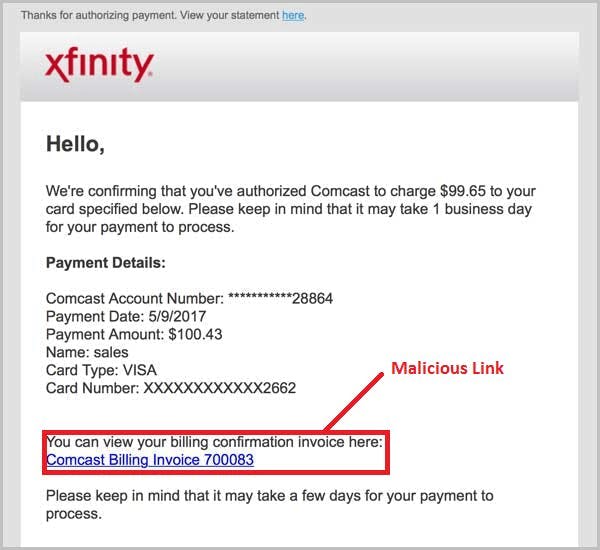
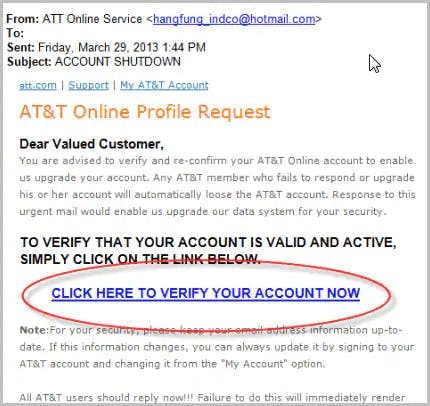
How can brands protect themselves and their customers?
Understanding brand impersonation