In this article
- An introduction to administrative units
- Manage administrative units
- How inheritance works for groups in administrative units
- Administrative units and Privileged Identity Management
- My Staff portal
- Limitations of administrative units
- FAQs
Blog Articles
Article at a glance
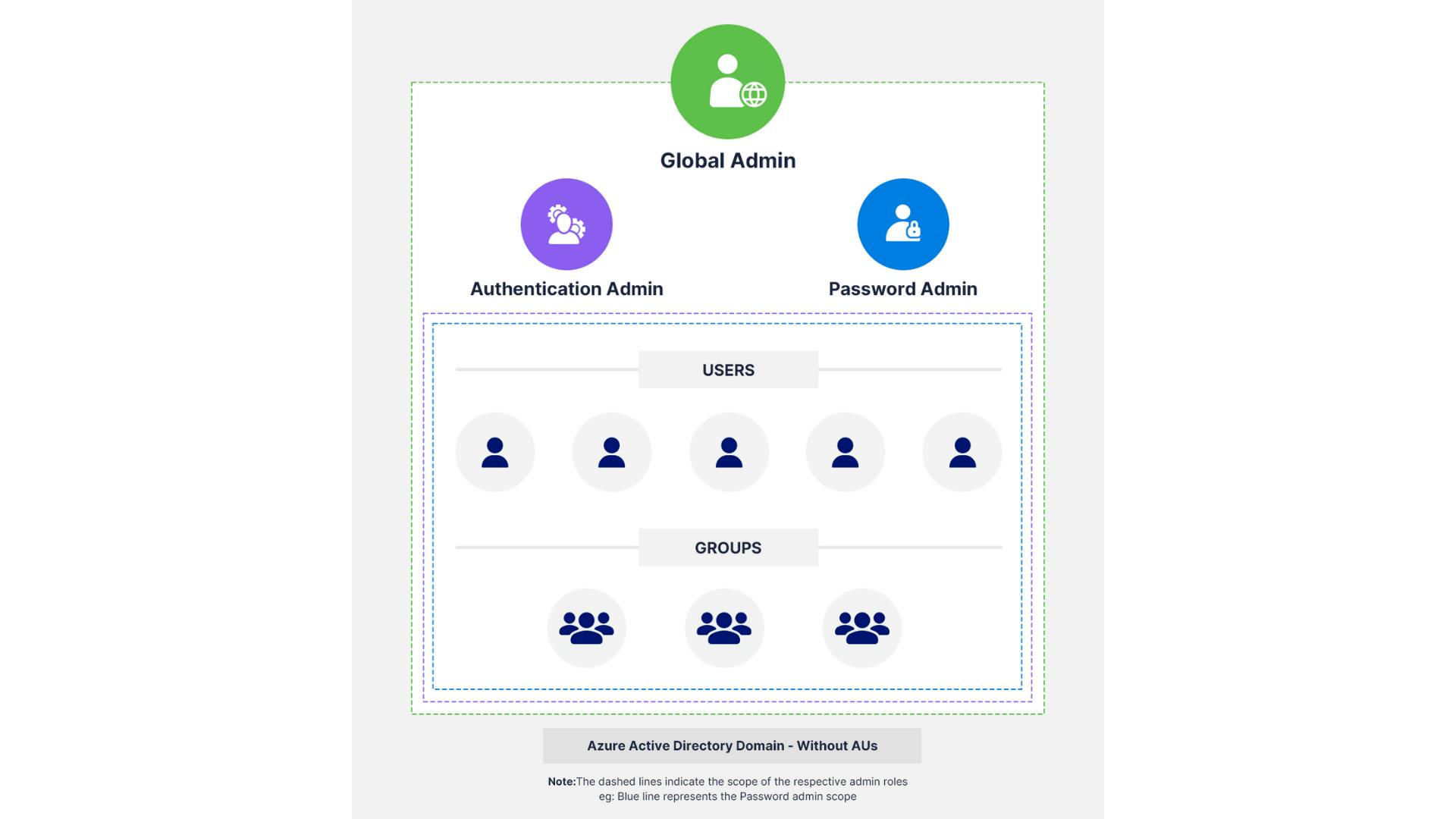
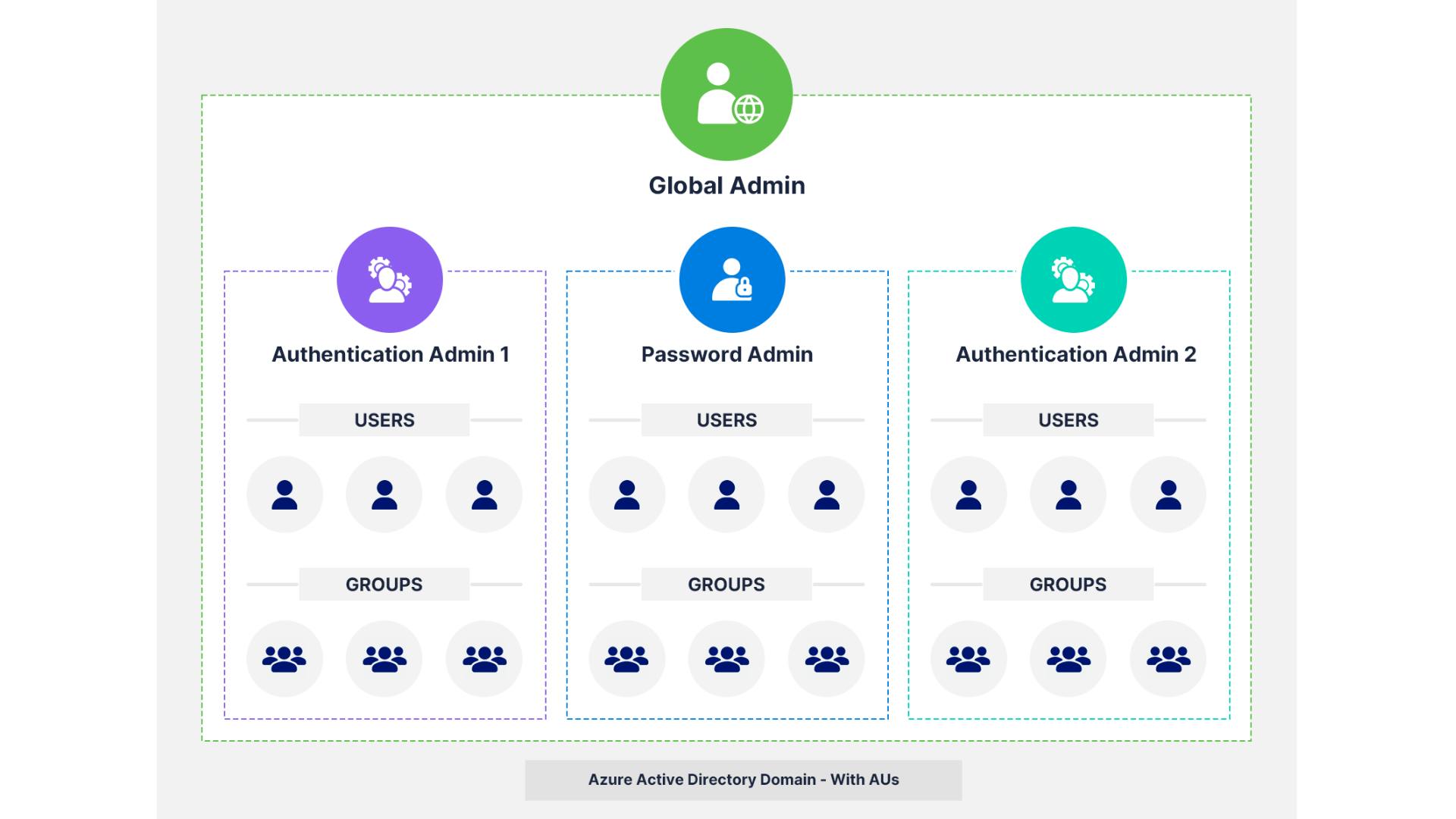
Azure AD Administrative Units (AUs) allow organizations to delegate admin roles with limited scope, reducing the need for global admin access and supporting the principle of least privilege. However, AUs have limitations:
- AUs can only contain users and groups, not devices. They require Azure AD Premium licenses, and not all administrative roles are available for AUs.
Read more
An introduction to Azure AD administrative units
Why do you need administrative units?
Manage administrative units in Azure Active Directory
Licensing requirements
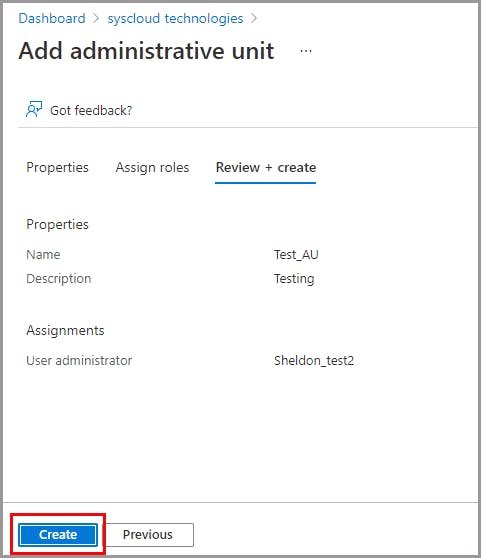
Create an administrative unit
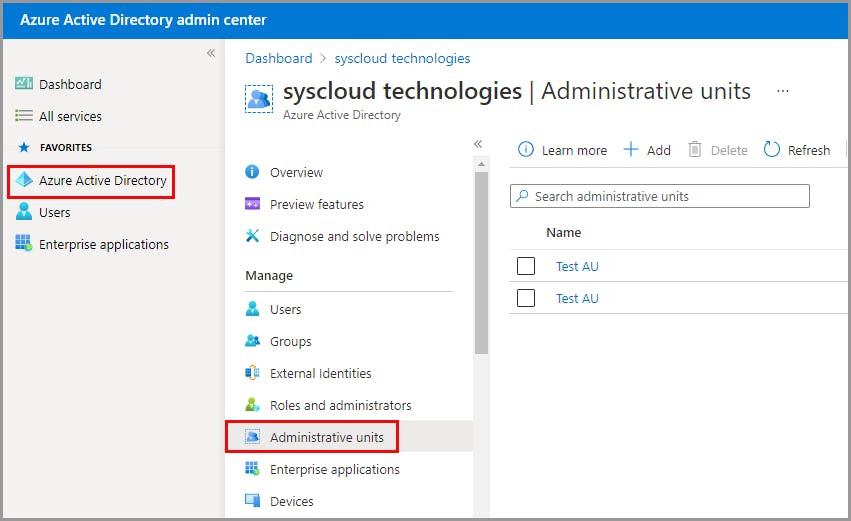
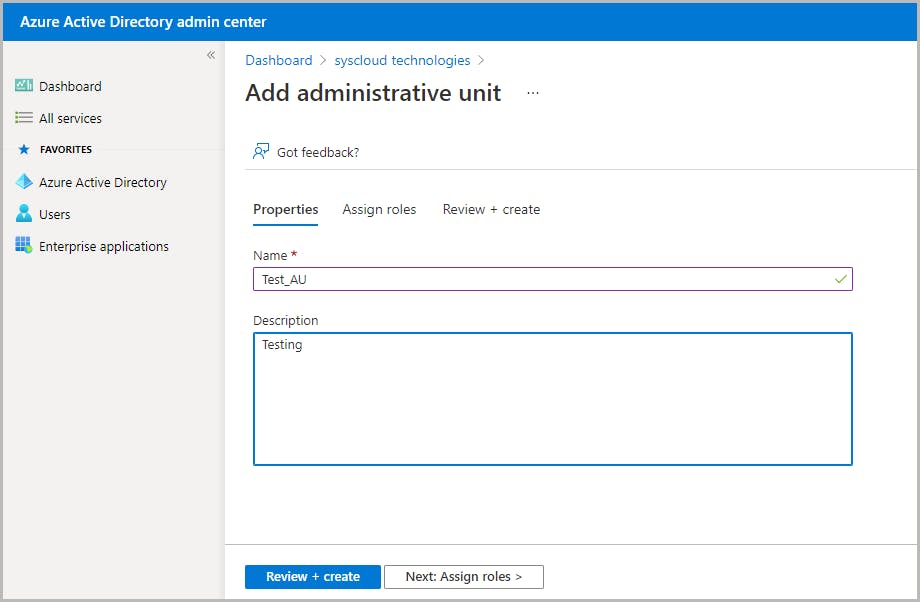
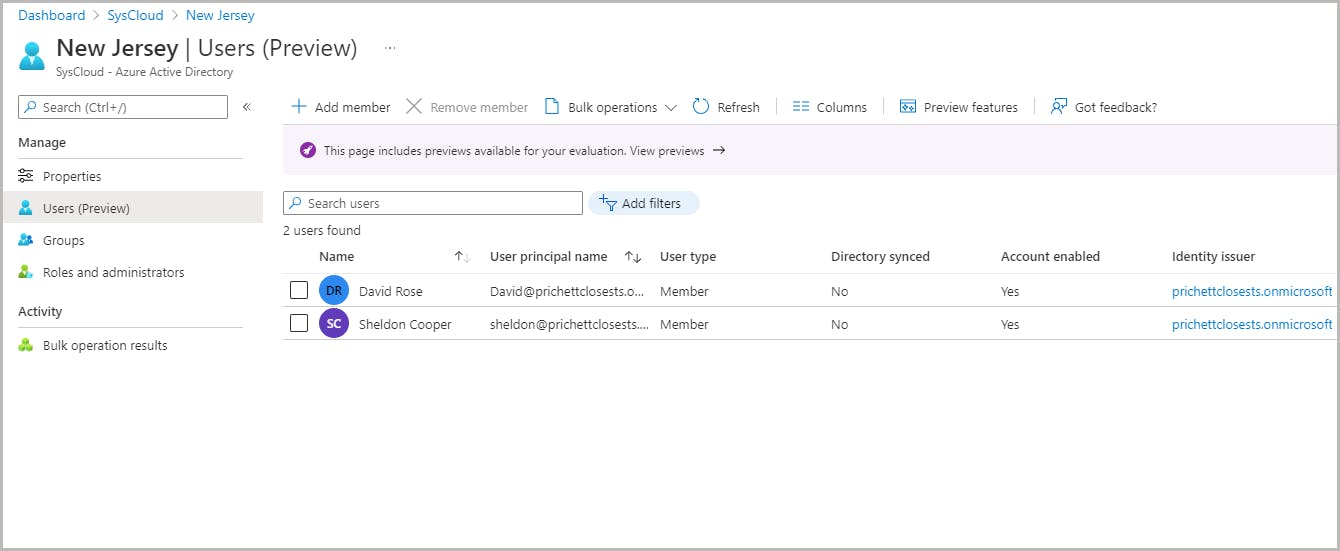
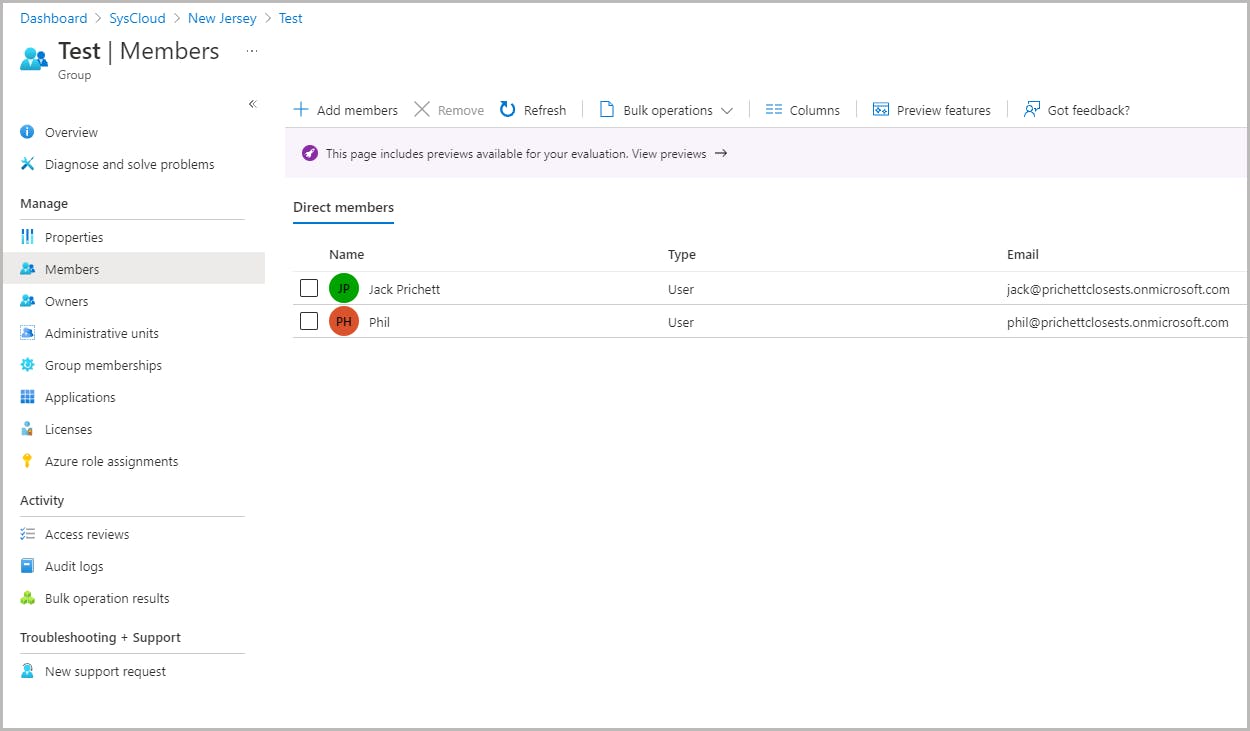
Add users to an administrative unit
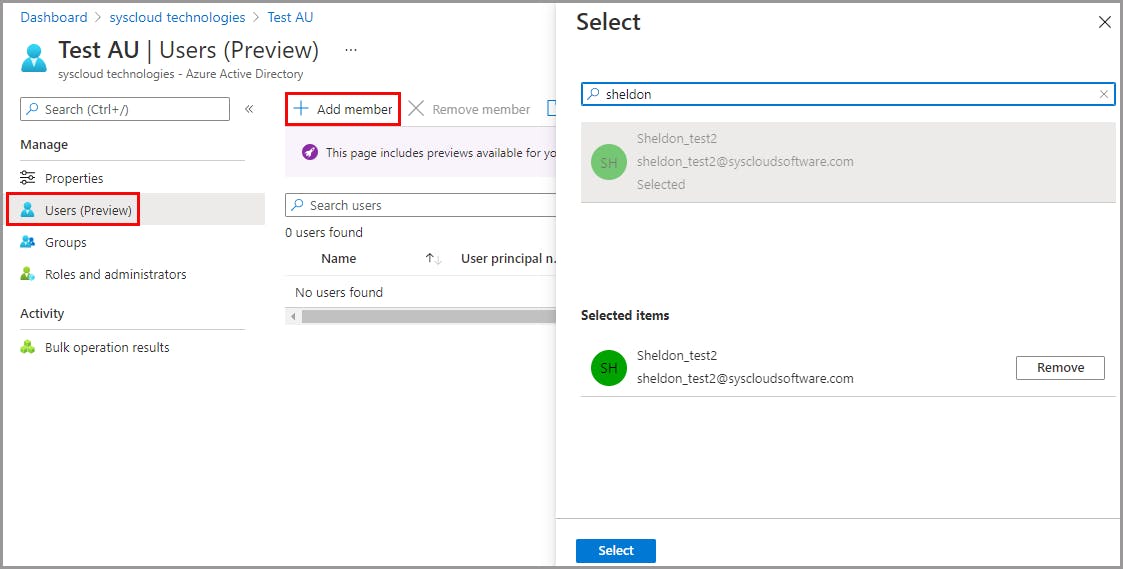
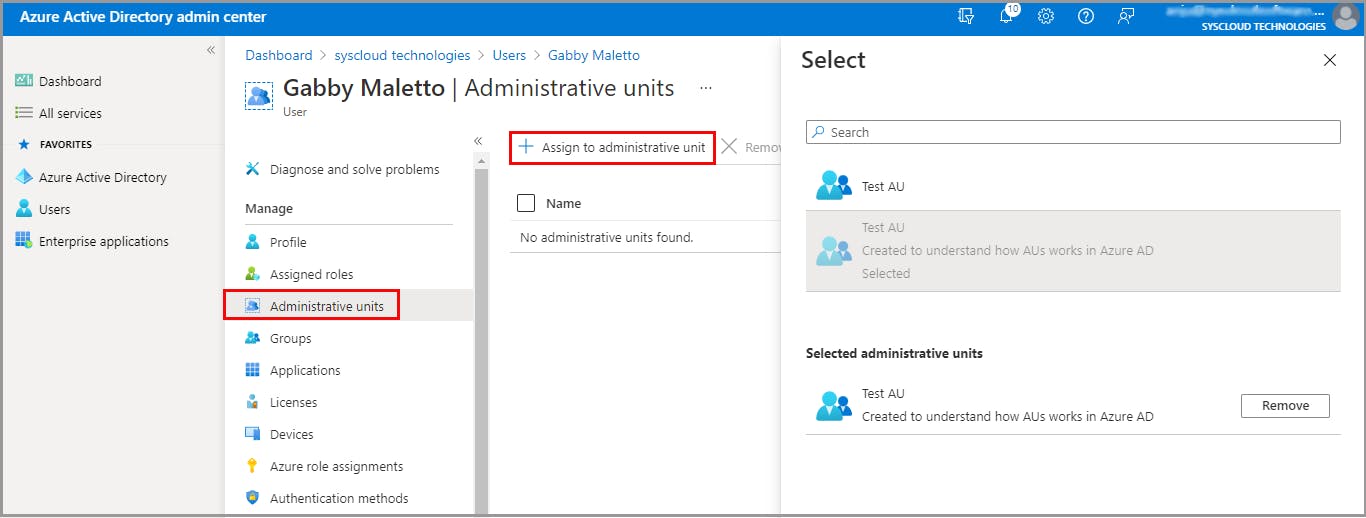

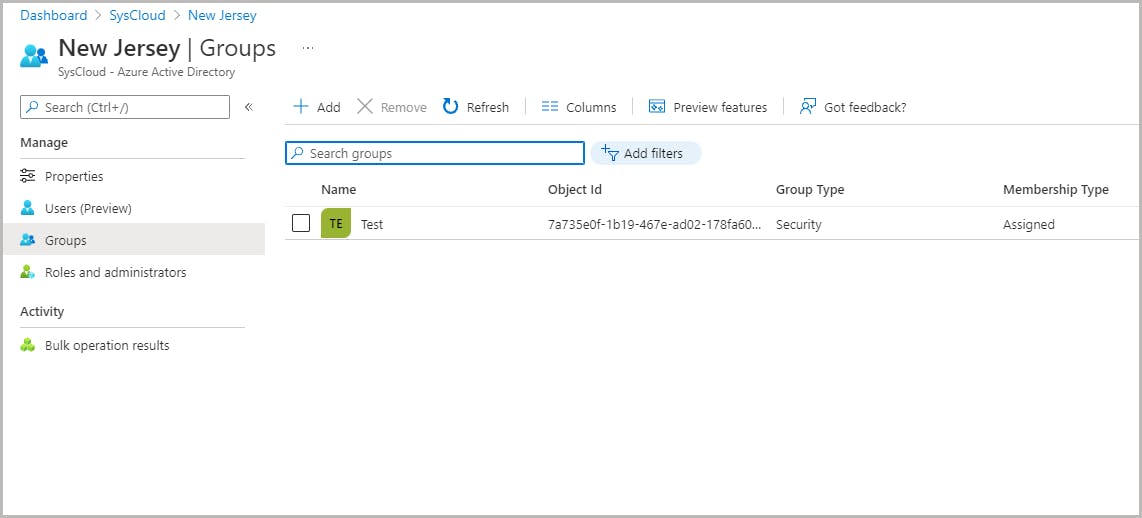
Add groups to an administrative unit
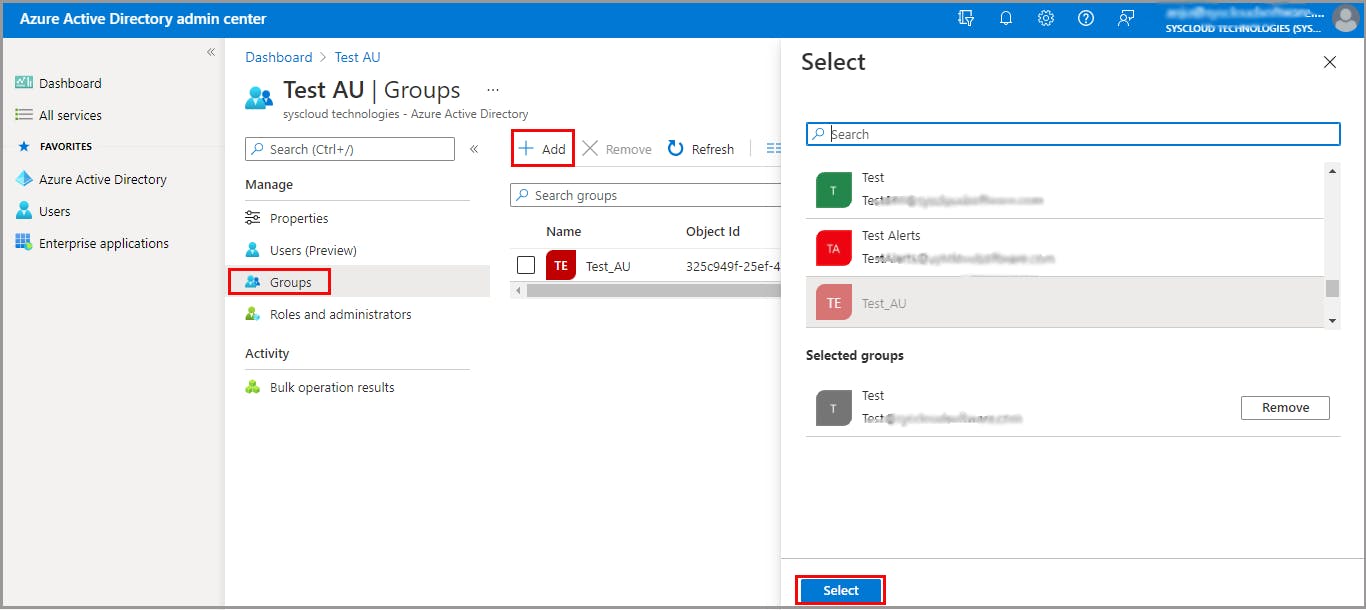
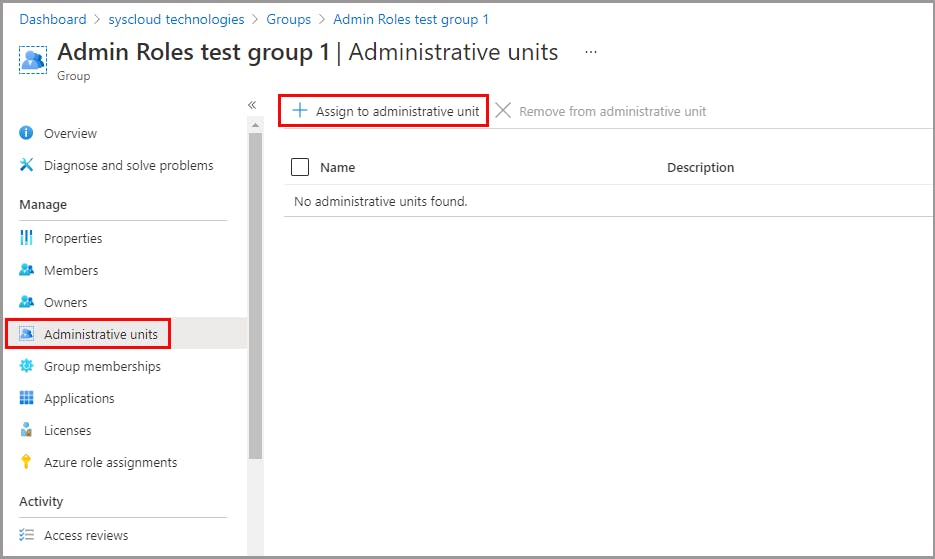
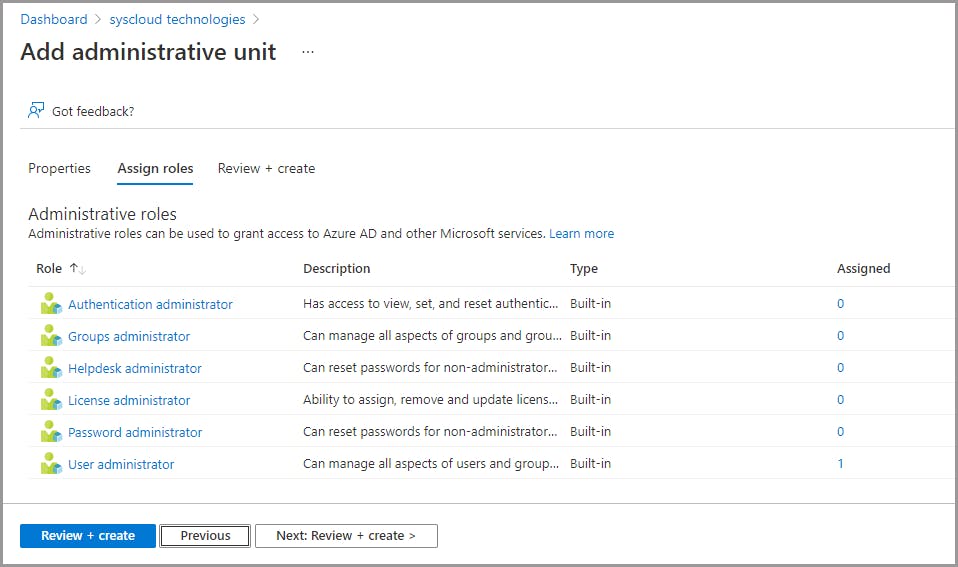
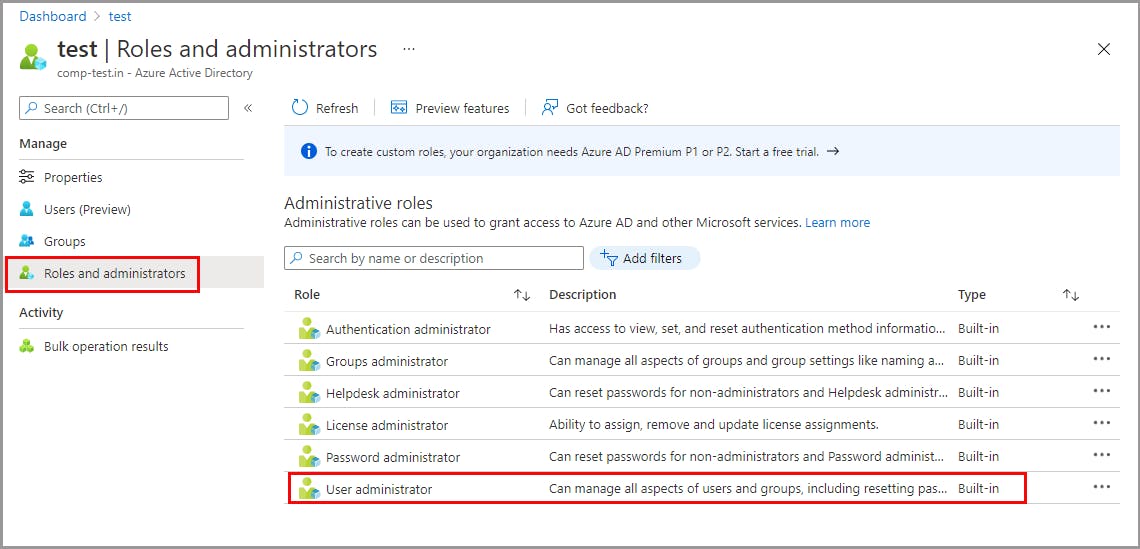
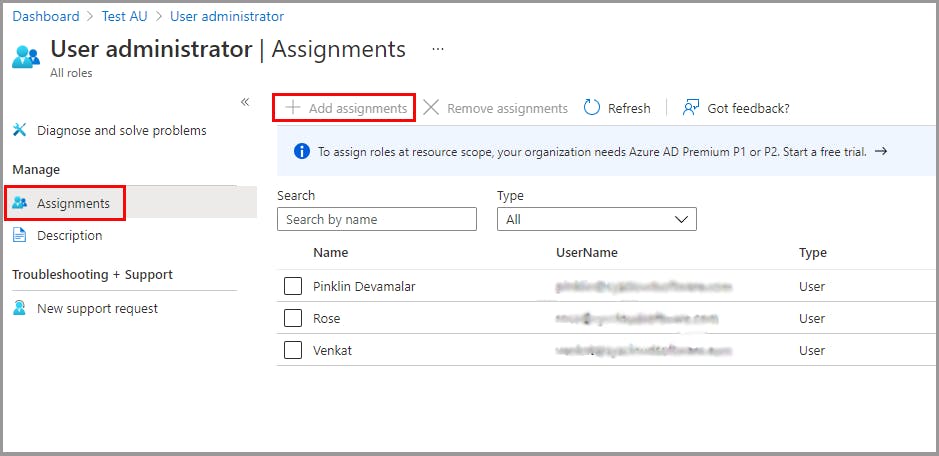
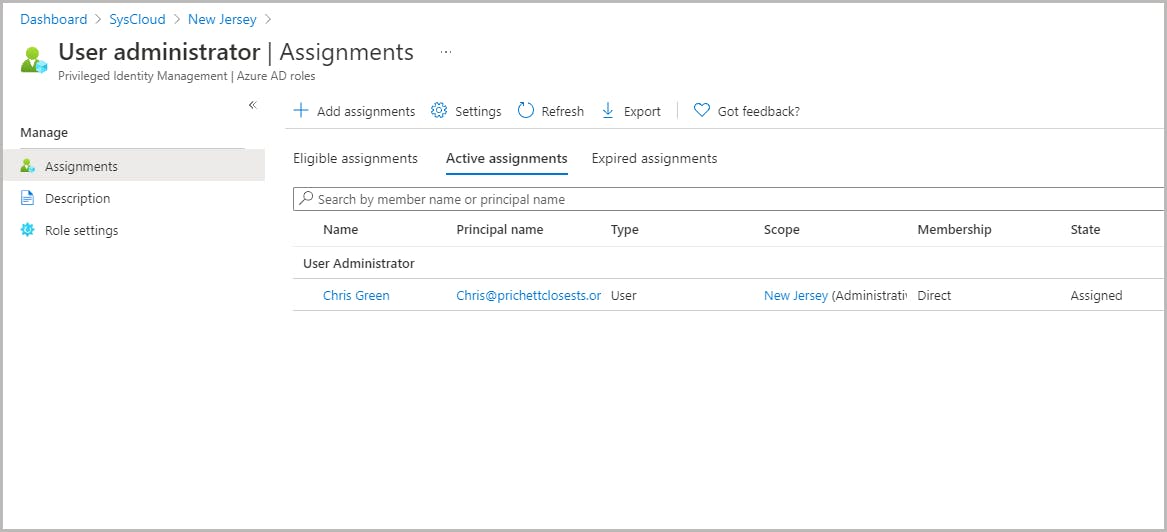
Assign admin roles for an administrative unit
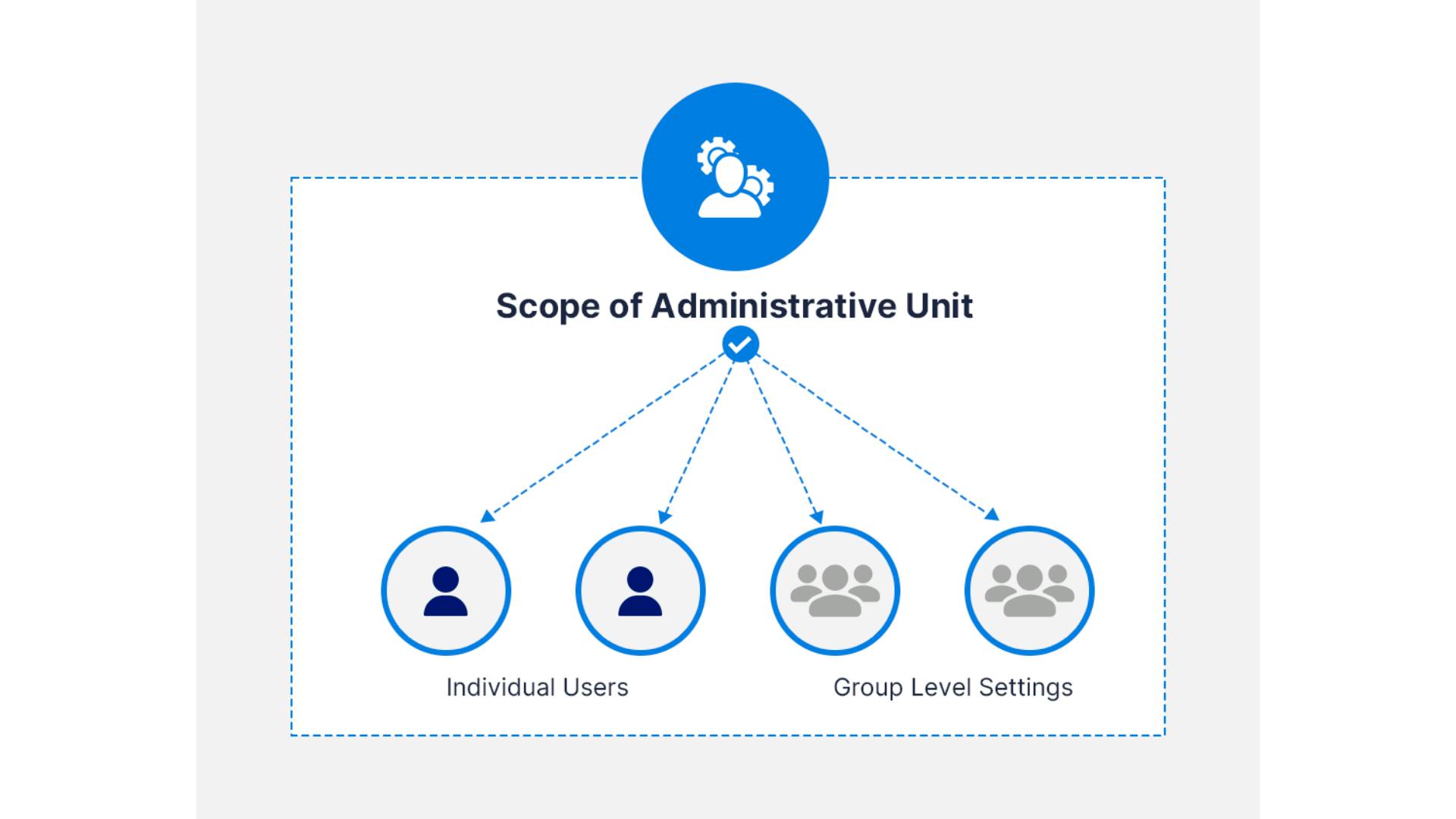
How inheritance works for groups in administrative units
Administrative units and Privileged Identity Management
Key features of Privileged Identity Management
Assign scoped roles in Privileged Identity Management
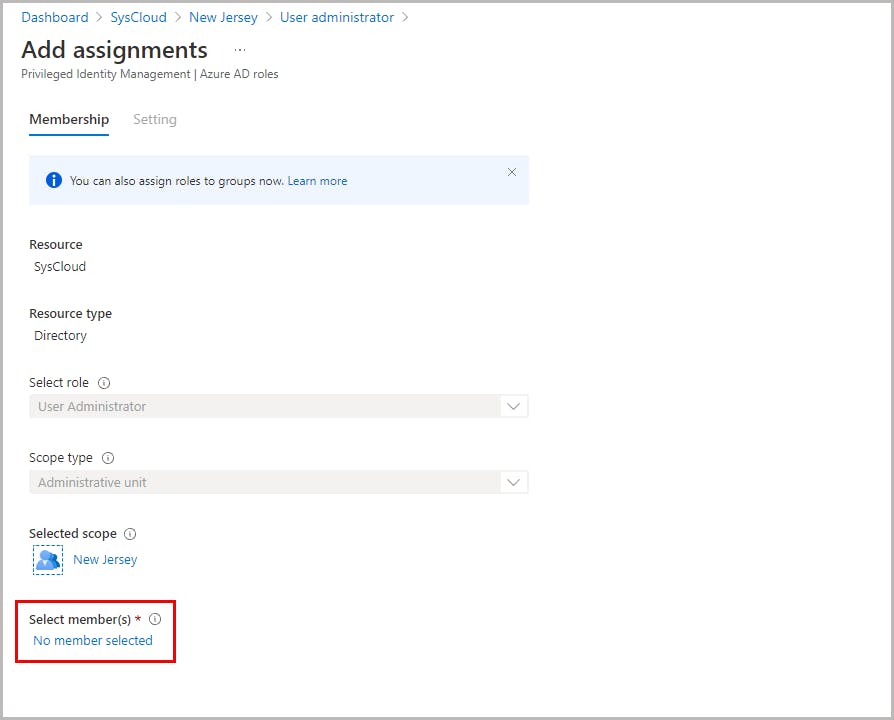

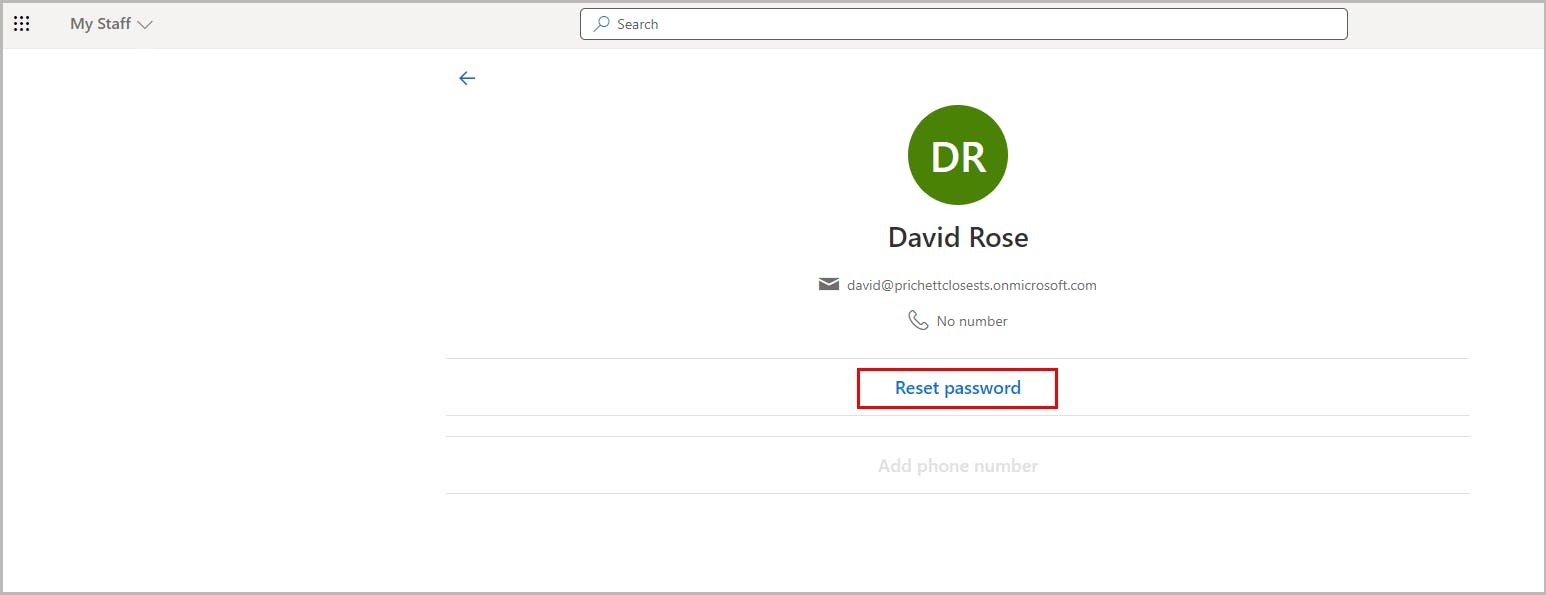
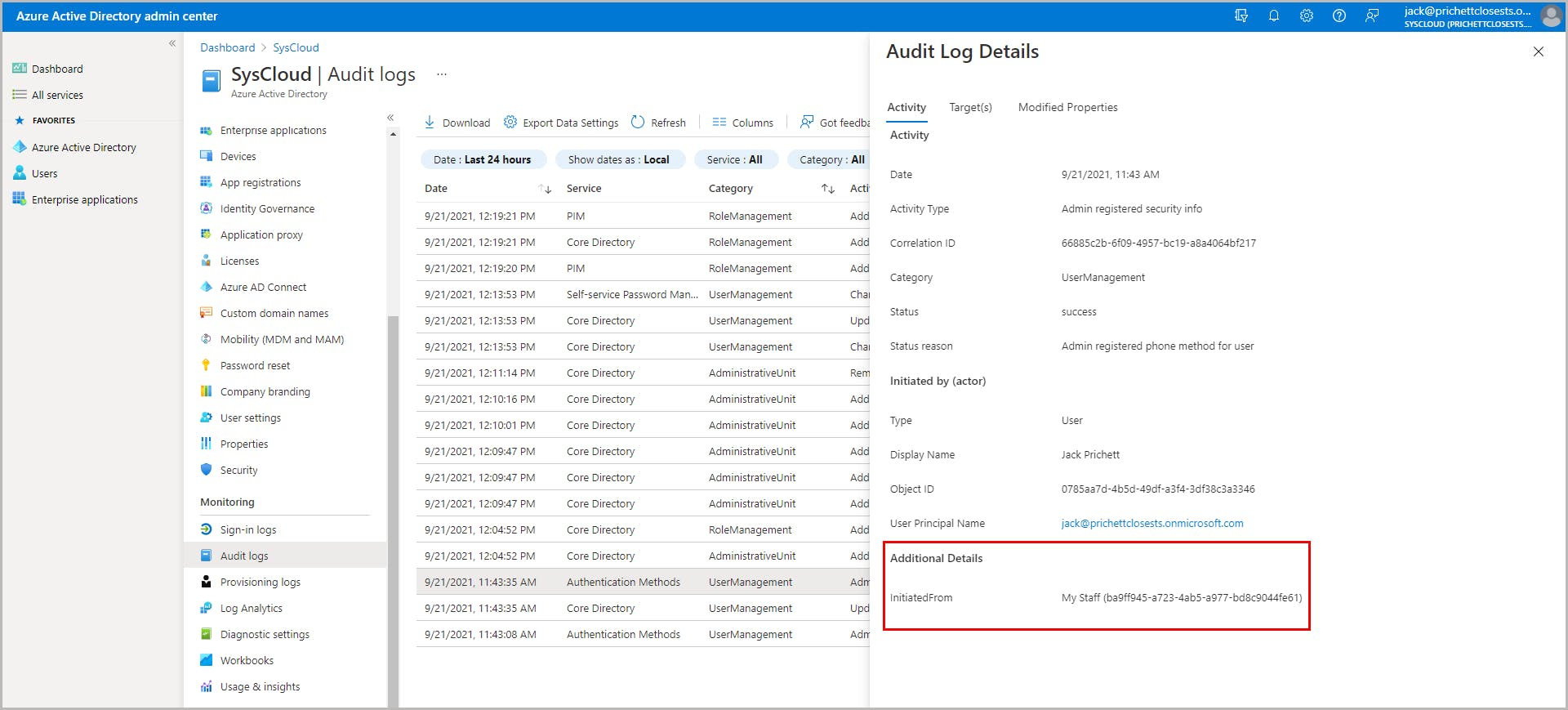
Administrative units and My Staff portal
How to enable My Staff in Azure Active Directory
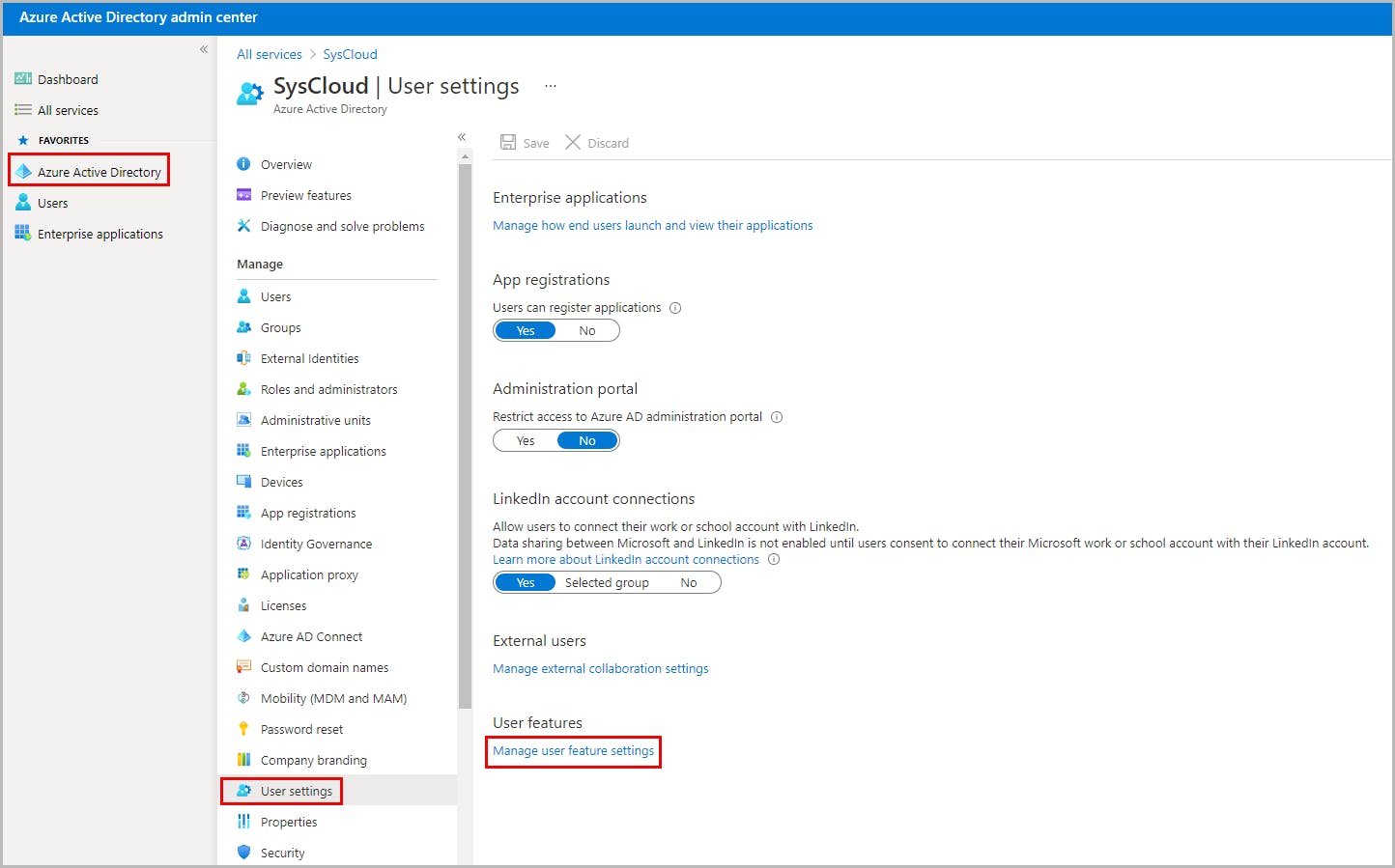
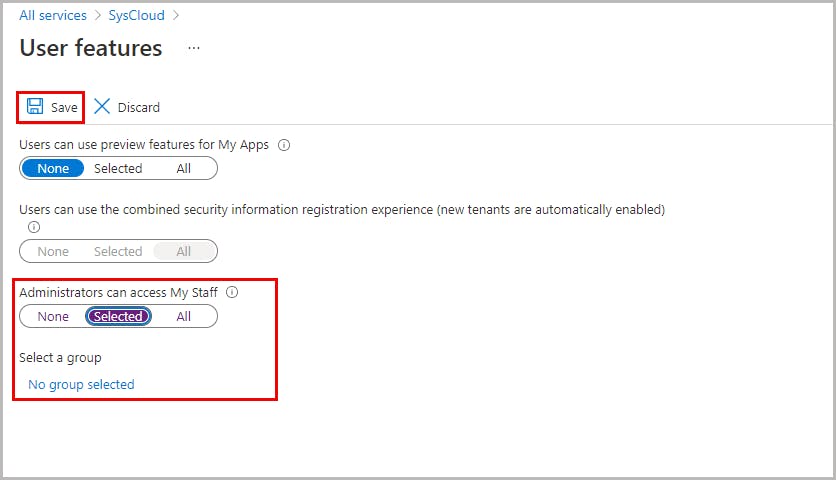
How My Staff works
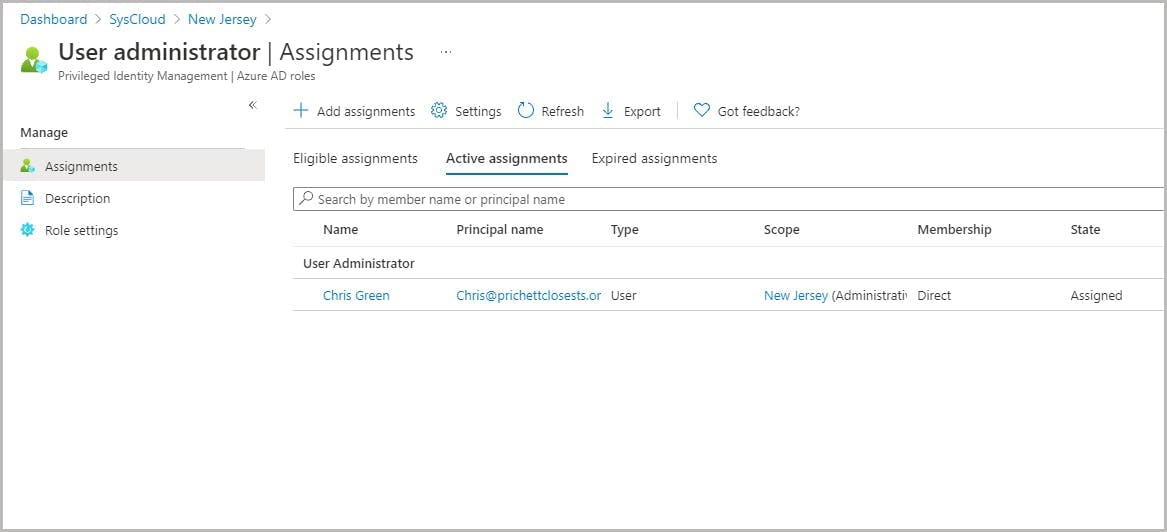

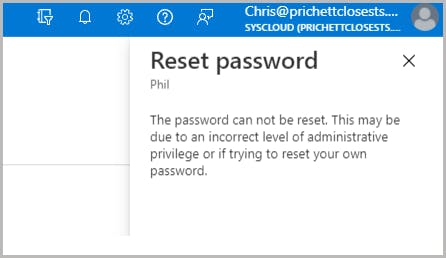
How to reset a user password